Simplify, automate & optimize with Unity Automation Center
Centralized automation to streamline workflows, optimize performance, and enhance your hybrid cloud efficiency.

Experience the power of automation with UnityOne.AI
Easily consolidate workflows, integrate tools across multicloud providers, monitor performance in real-time, and optimize your hybrid cloud environment for seamless operations and maximum efficiency.
Automation Center: Your Command Center for Multicloud Management
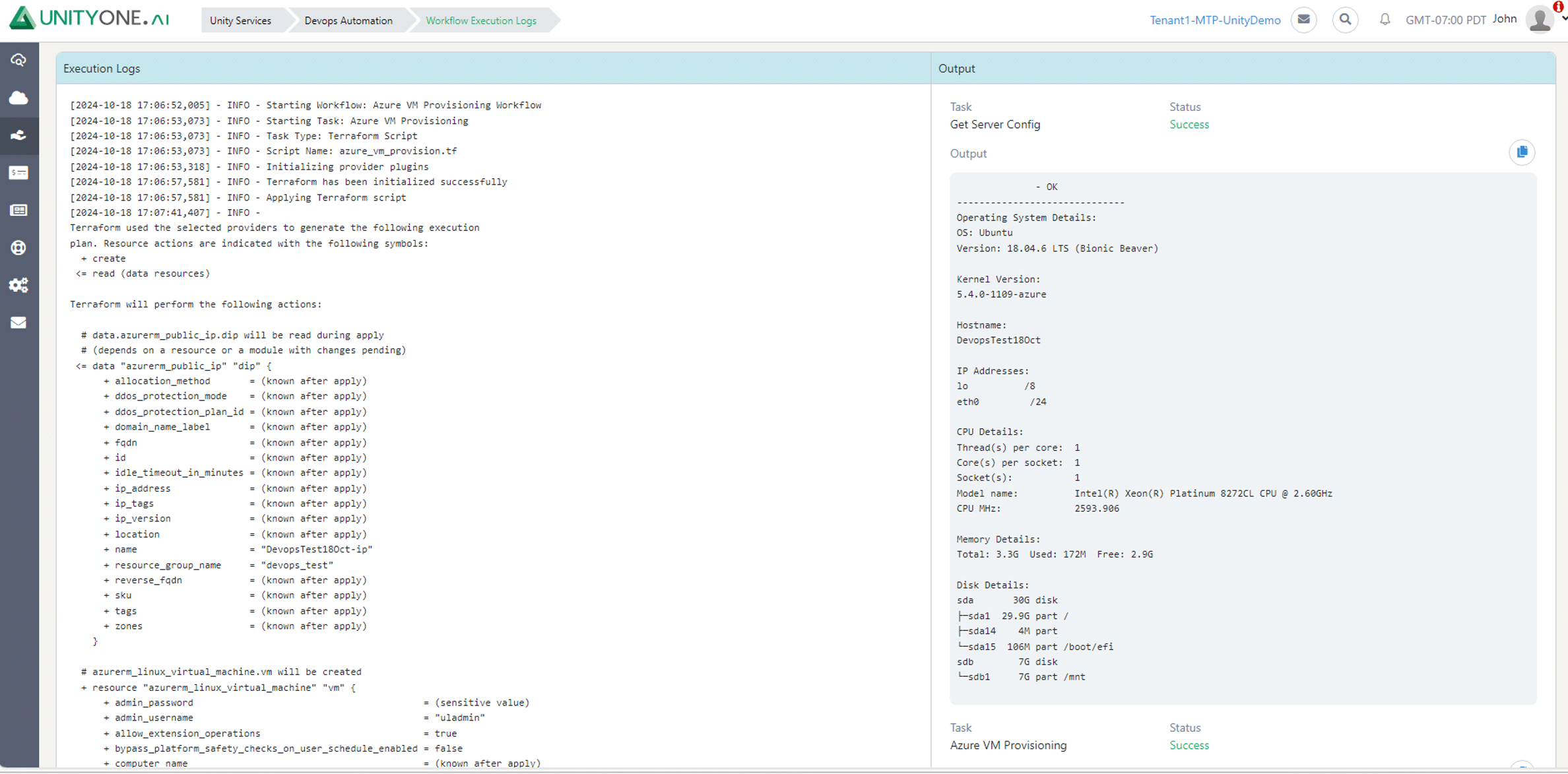
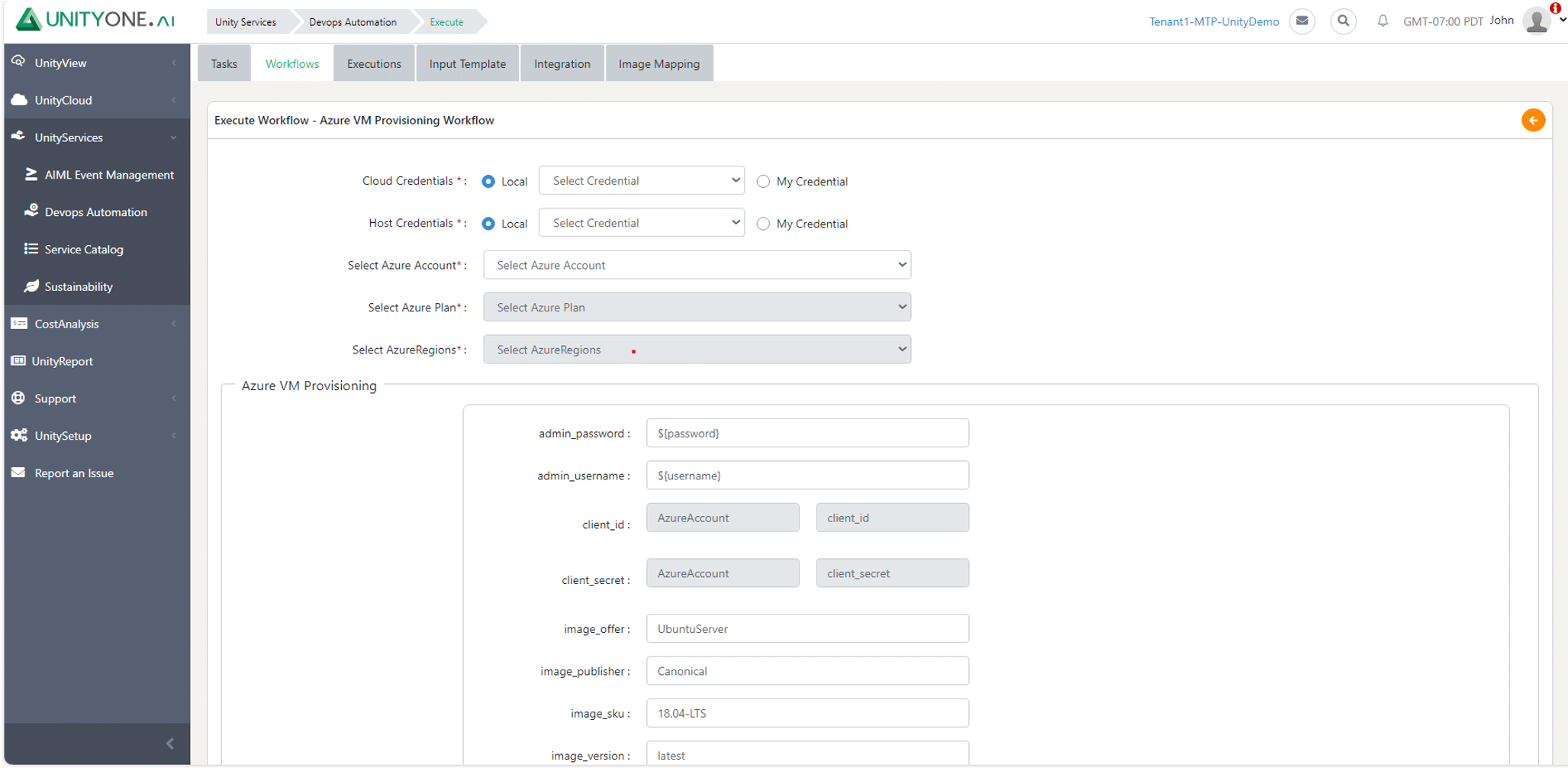
Azure VM Provisioning
Manual VM provisioning increases time to market and increases risk for human error; therefore, Automating the VM provisioning process, makes it faster and more efficient to meet business demands.
Automating VM Provisioning using Azure cloud allows to define variables and configure resources using Terraform scripts eliminating the need for manual configuration.
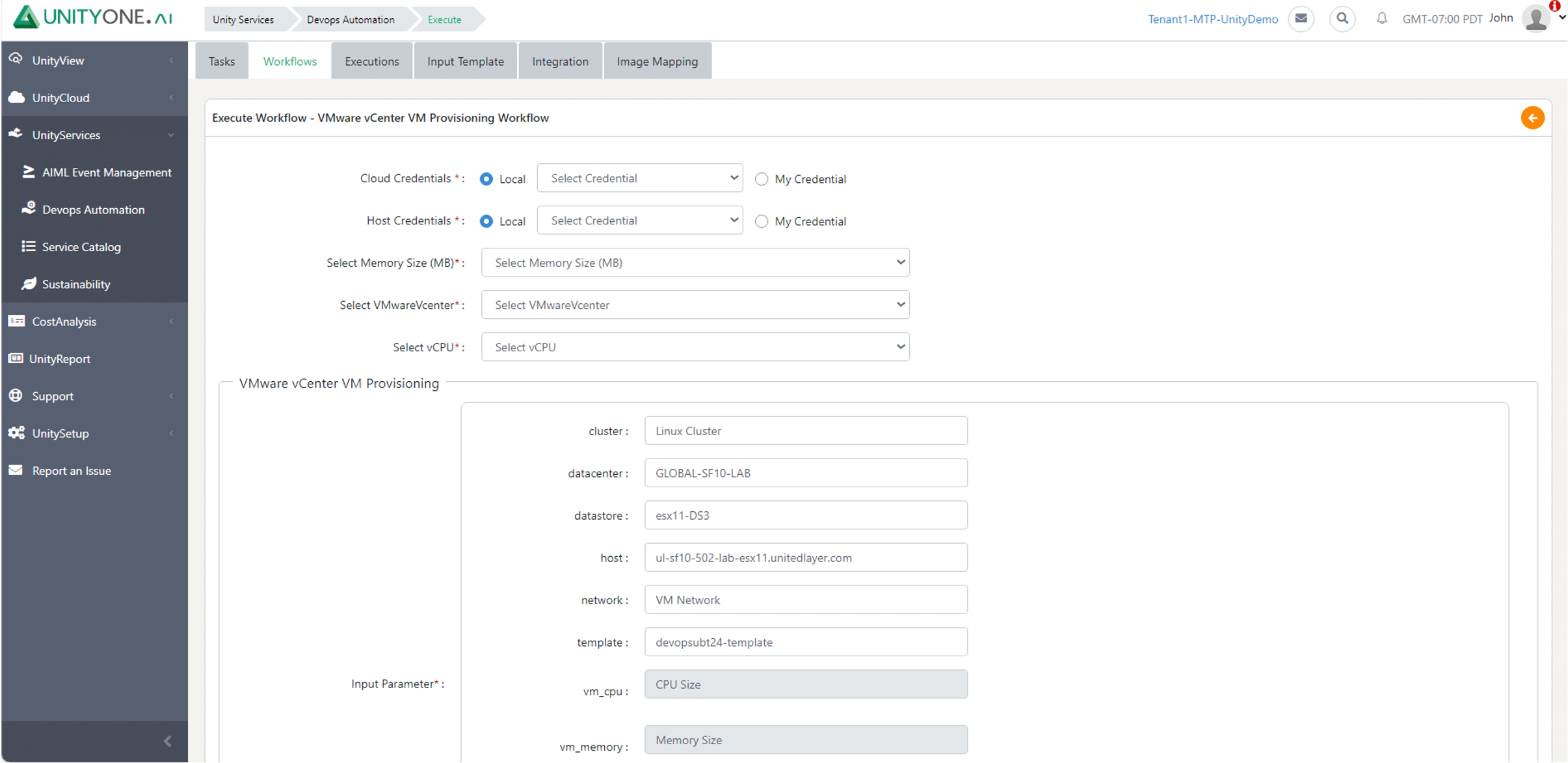
VMware vCenter VM Provisioning
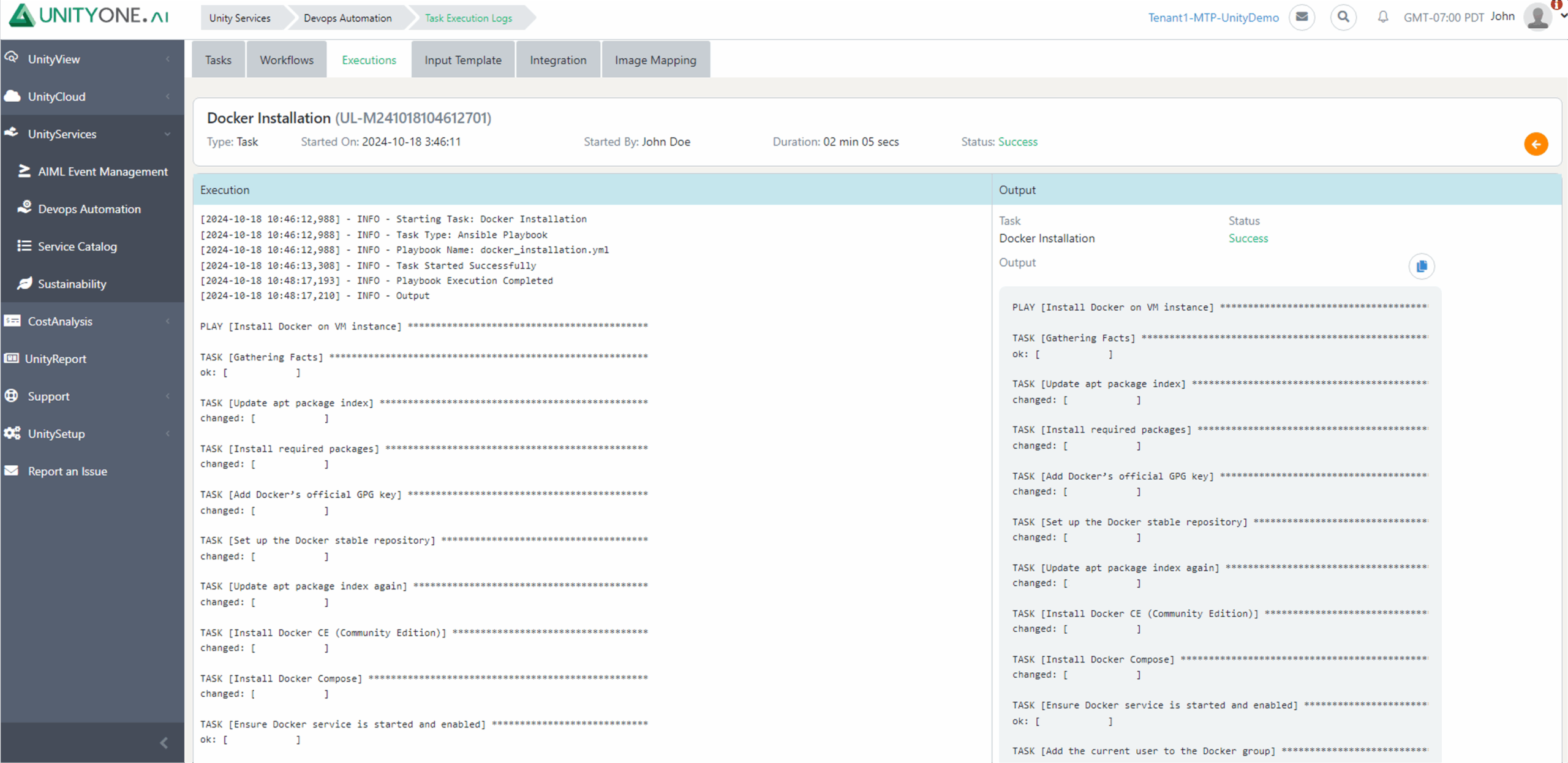
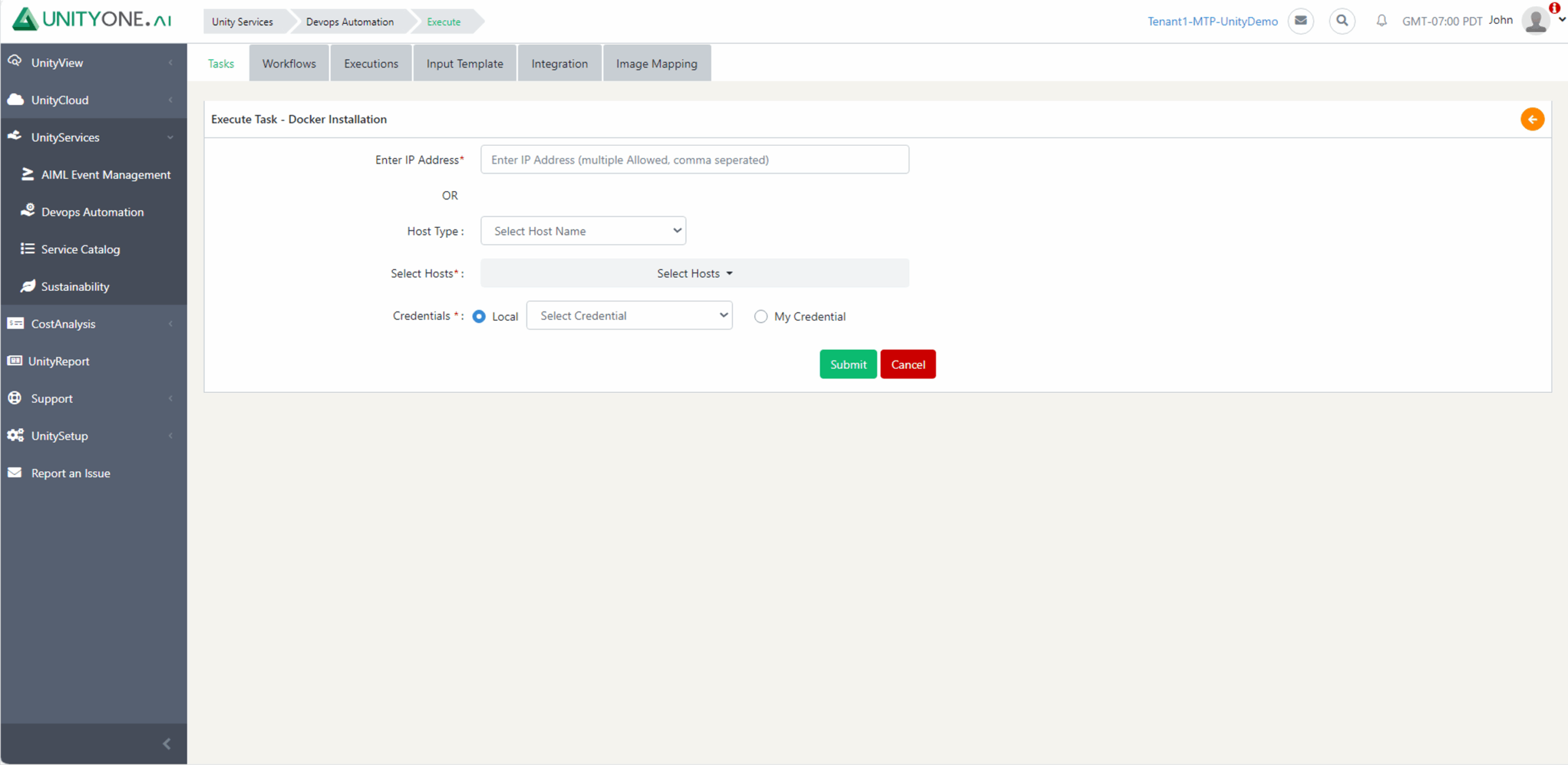
Docker Provisioning
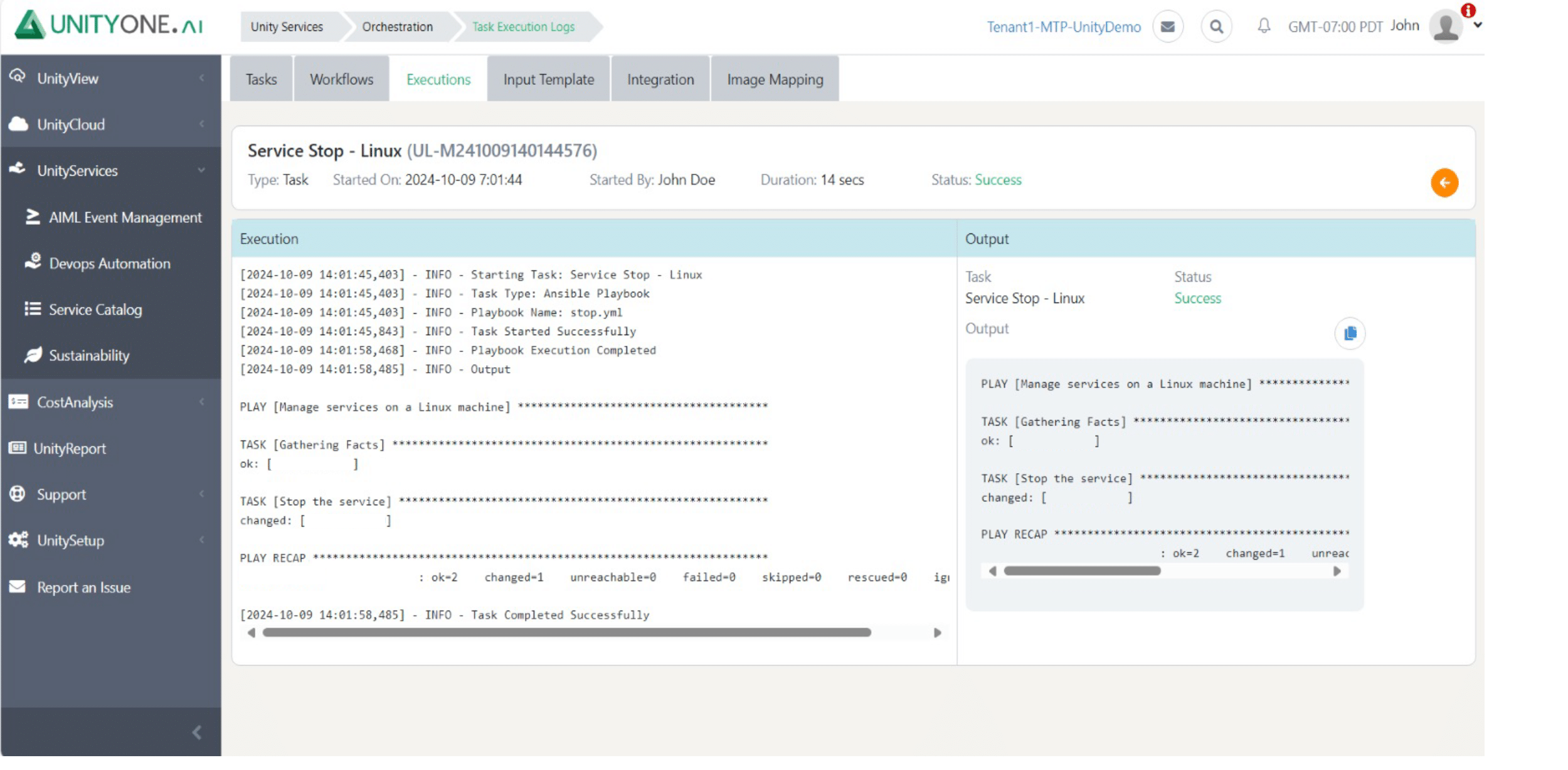
Service Stop
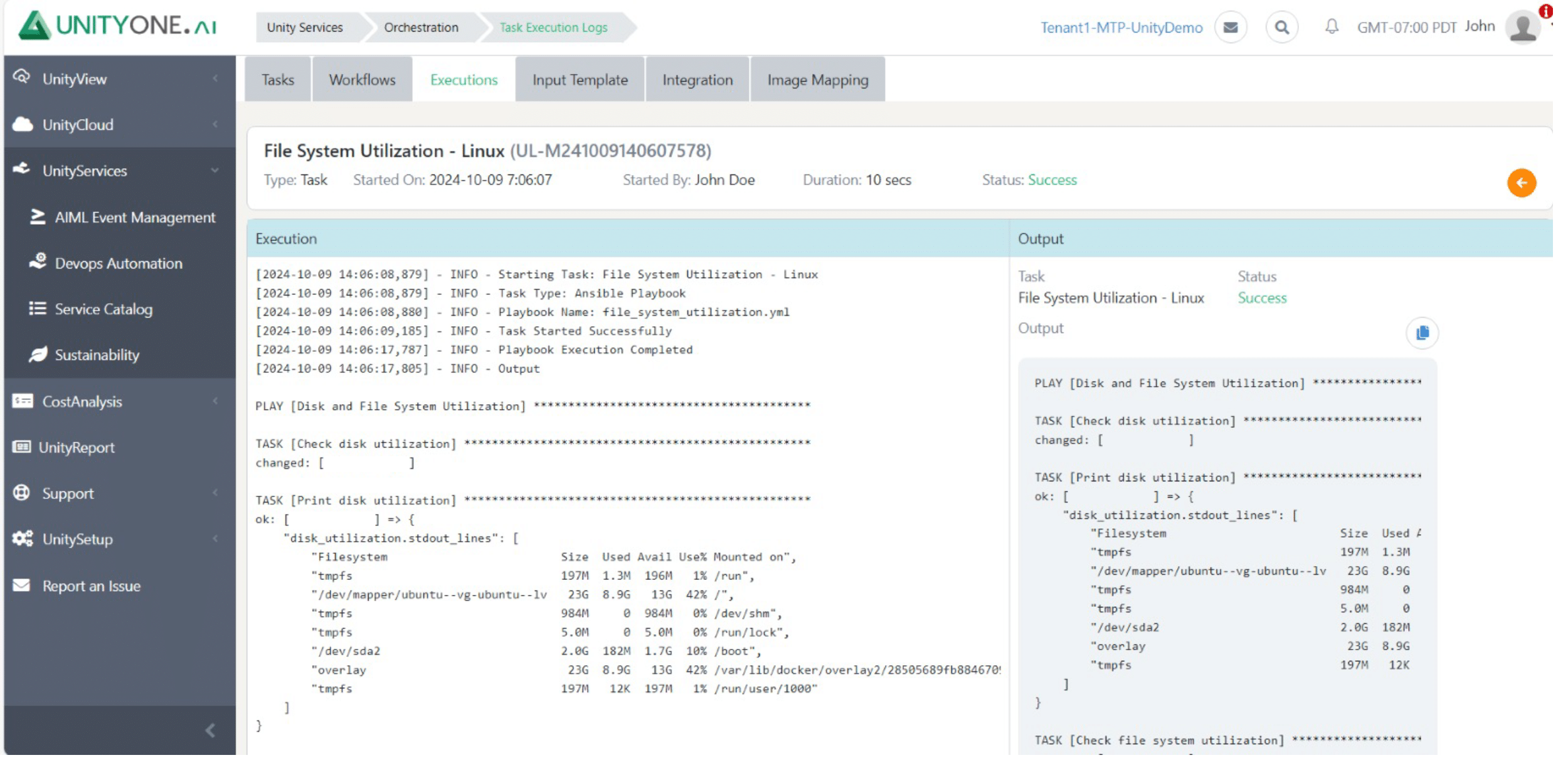
File System Utilization
Assessing file system utilization provides insights into disk usage patterns, helping to optimize storage resources effectively.
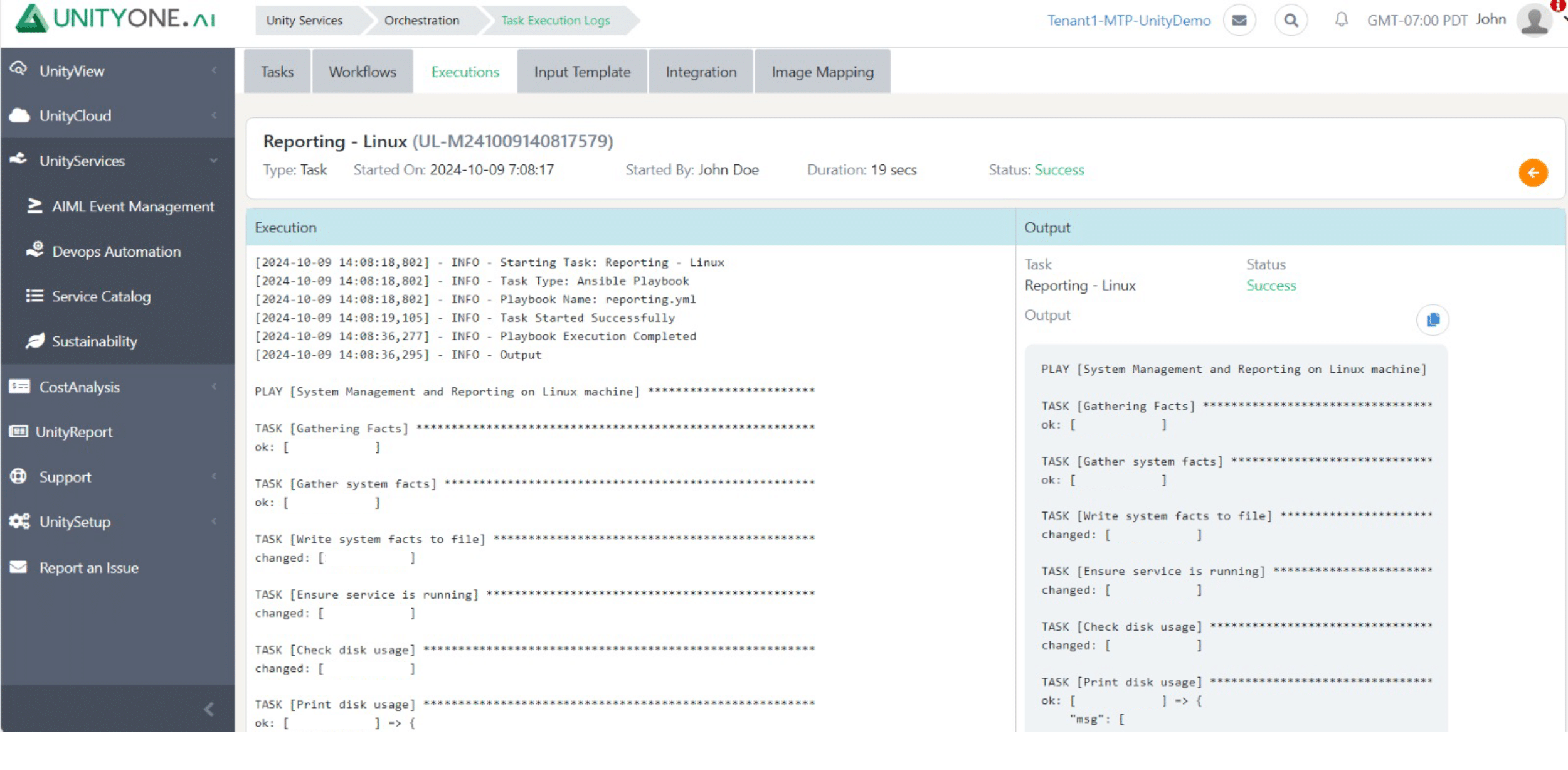
Reporting
Manual VM provisioning increases time to market and increases risk for human error; therefore, Automating the VM provisioning process, makes it faster and more efficient to meet business demands.
Automating VM Provisioning using Azure cloud allows to define variables and configure resources using Terraform scripts eliminating the need for manual configuration.
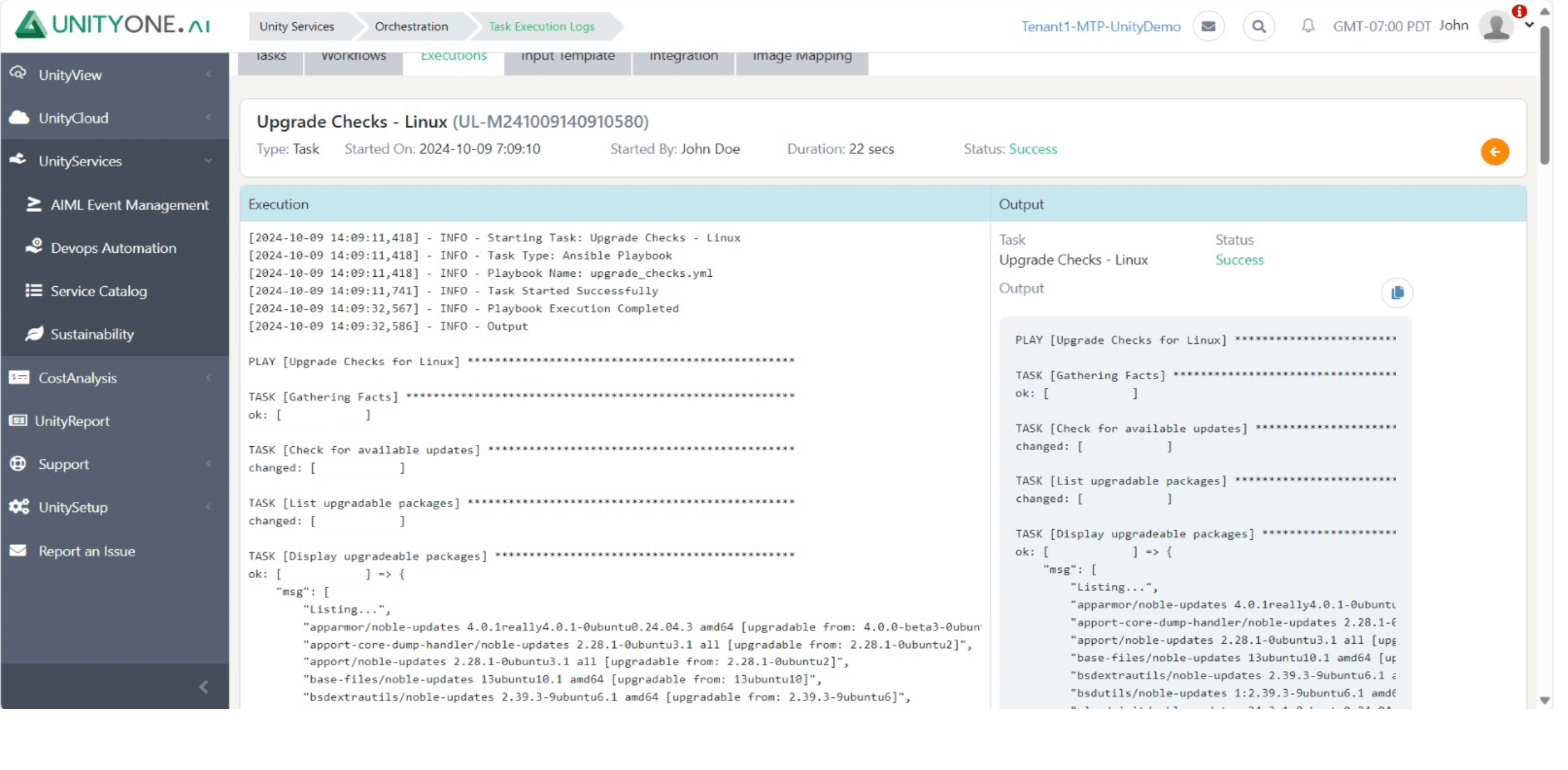
Upgrade Checks
Outdated systems can expose organizations to security vulnerabilities and performance issues, making regular upgrade checks essential for maintaining system integrity.
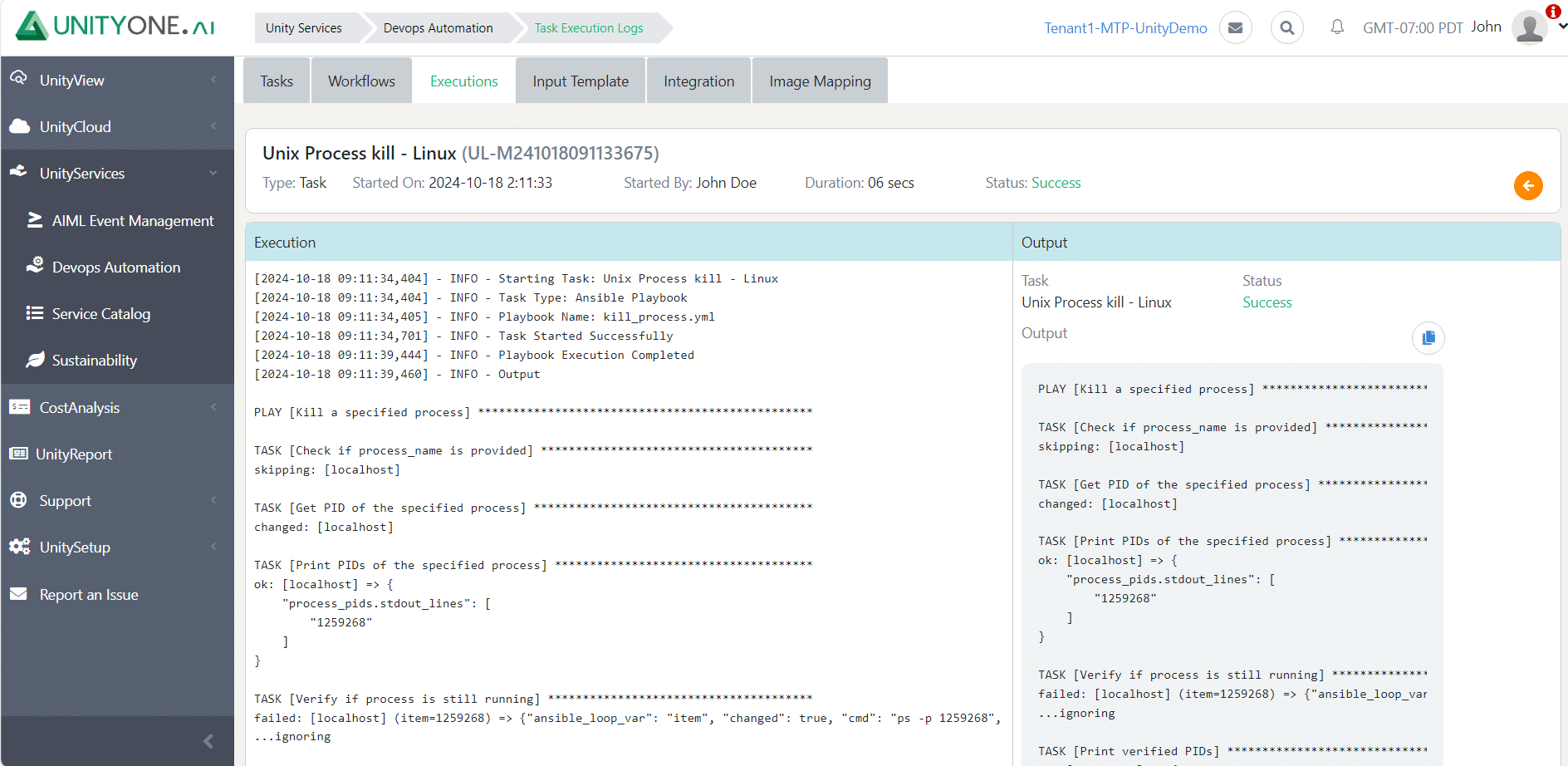
Unix Process Kill
Allowing problematic processes to run unchecked can lead to system slowdowns or crashes, negatively impacting overall operational efficiency.
Terminating unresponsive or resource-intensive processes helps free up system resources, ensuring optimal performance for critical applications.
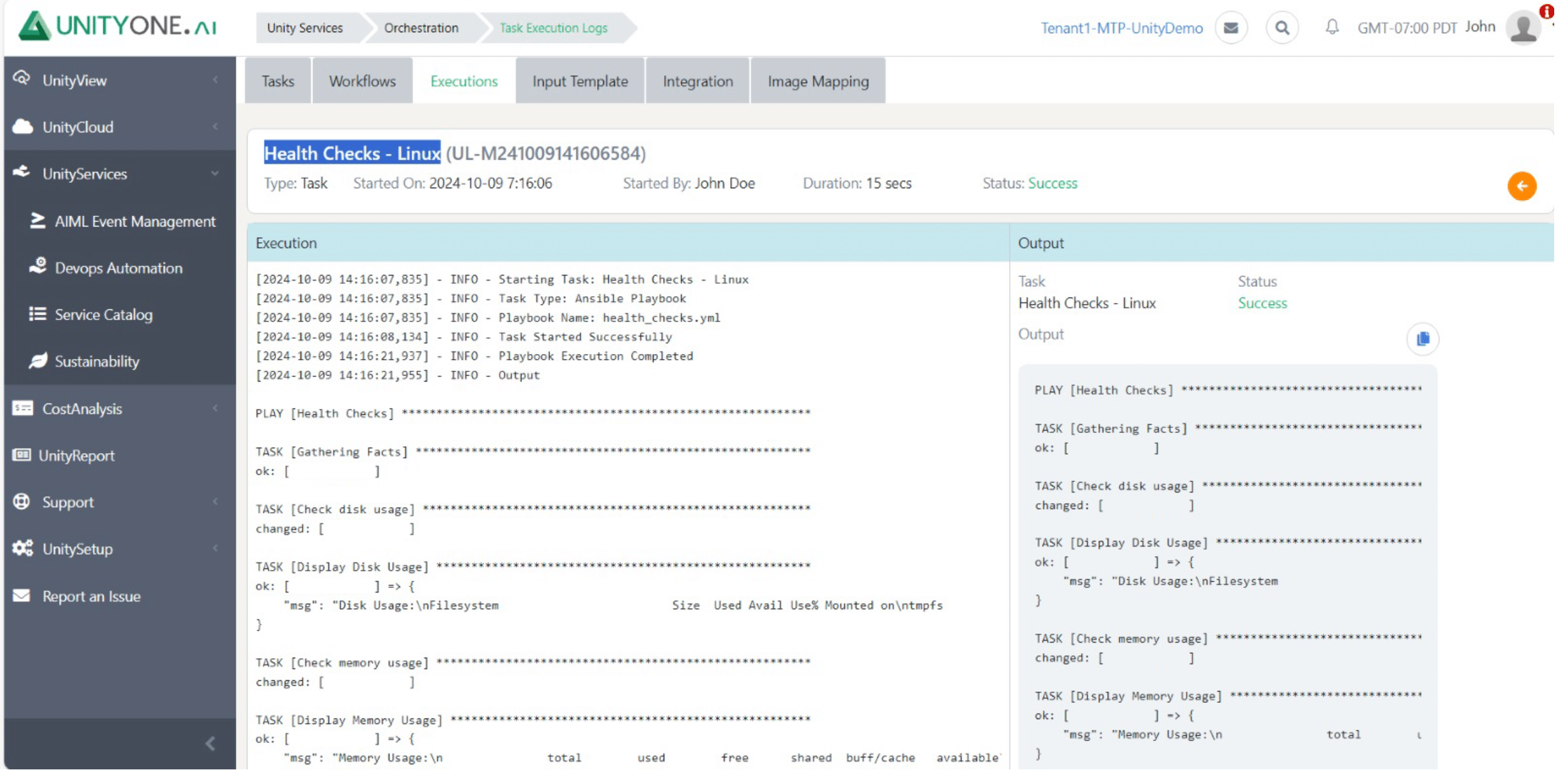
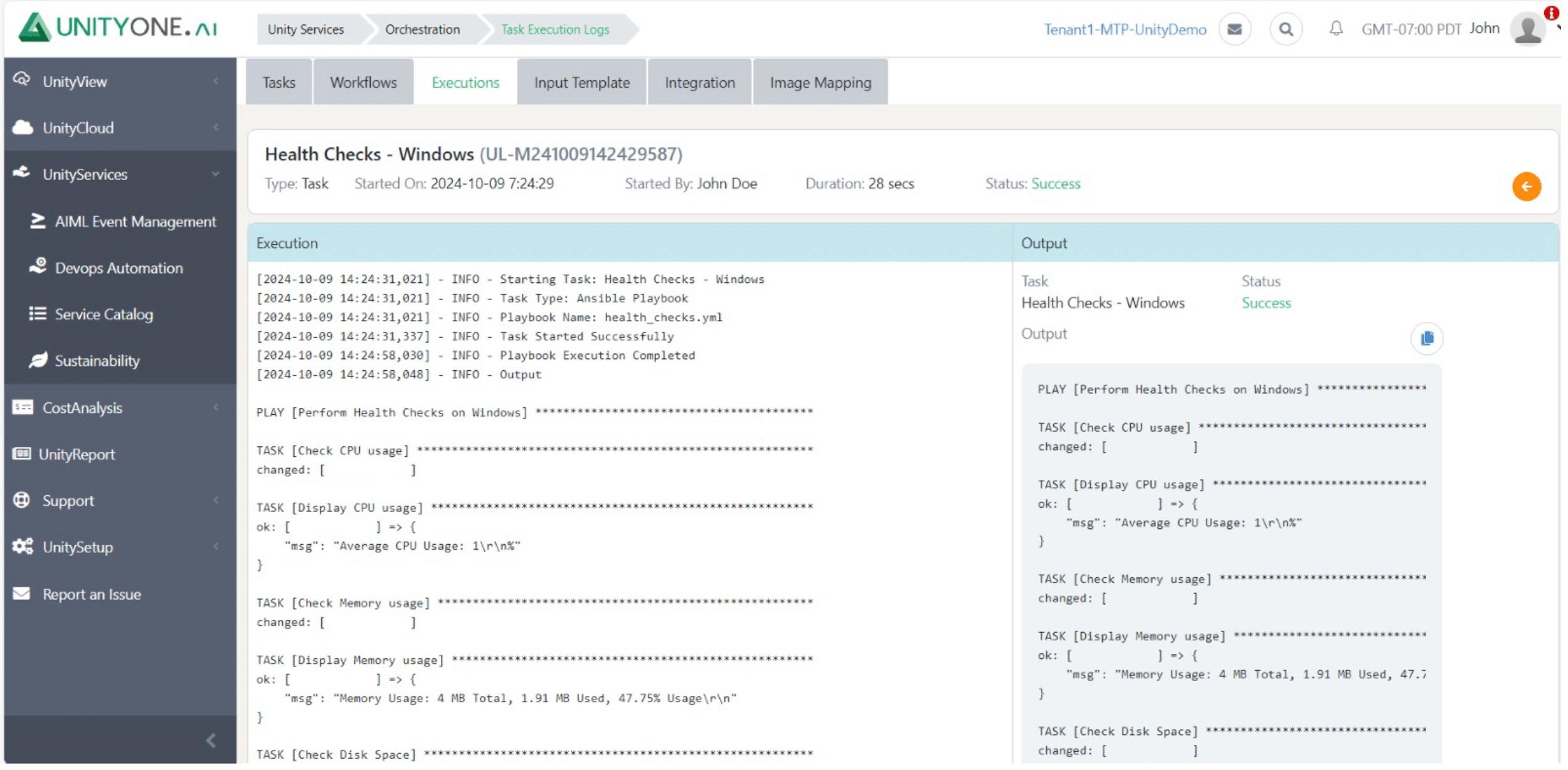
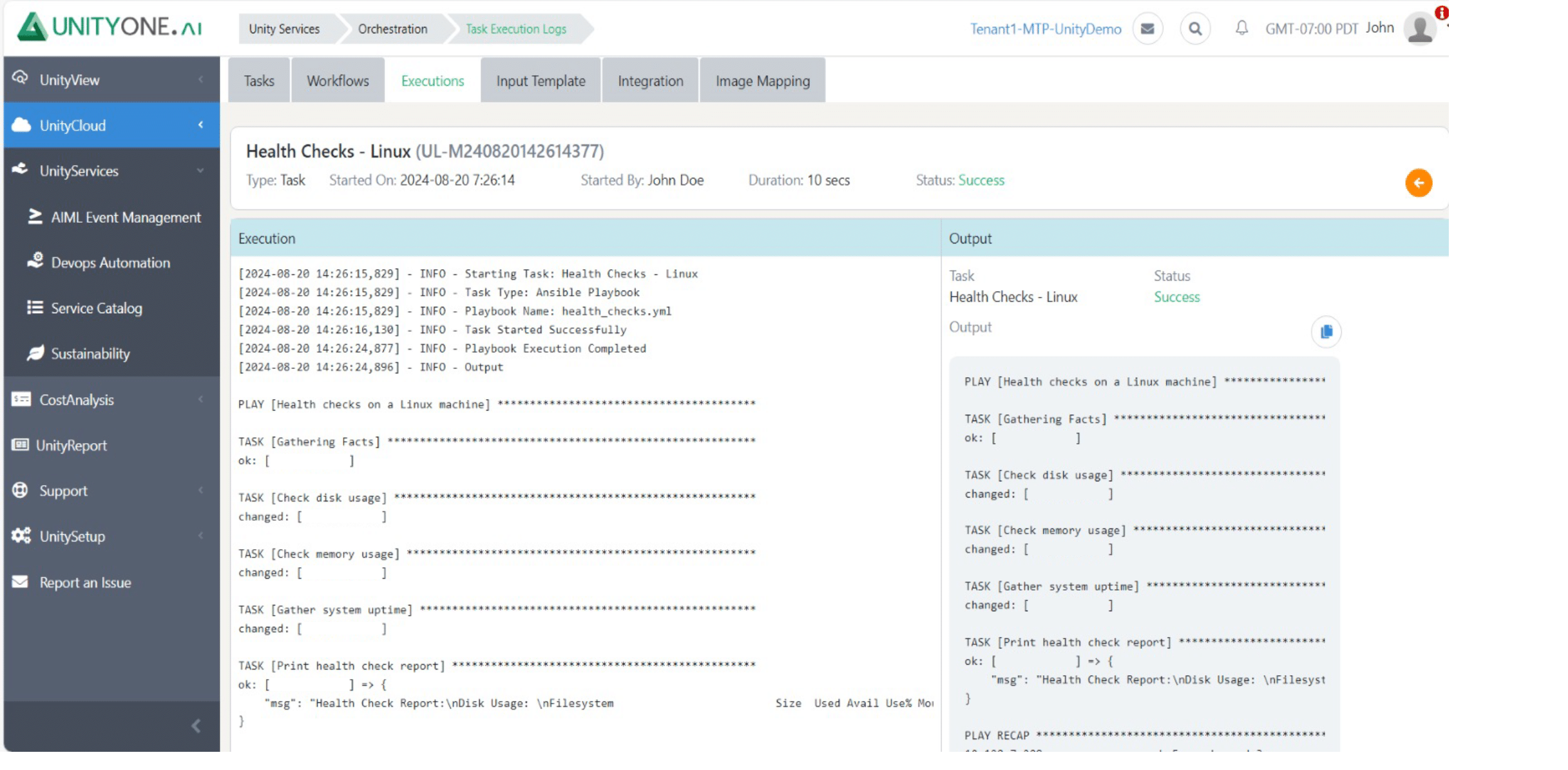
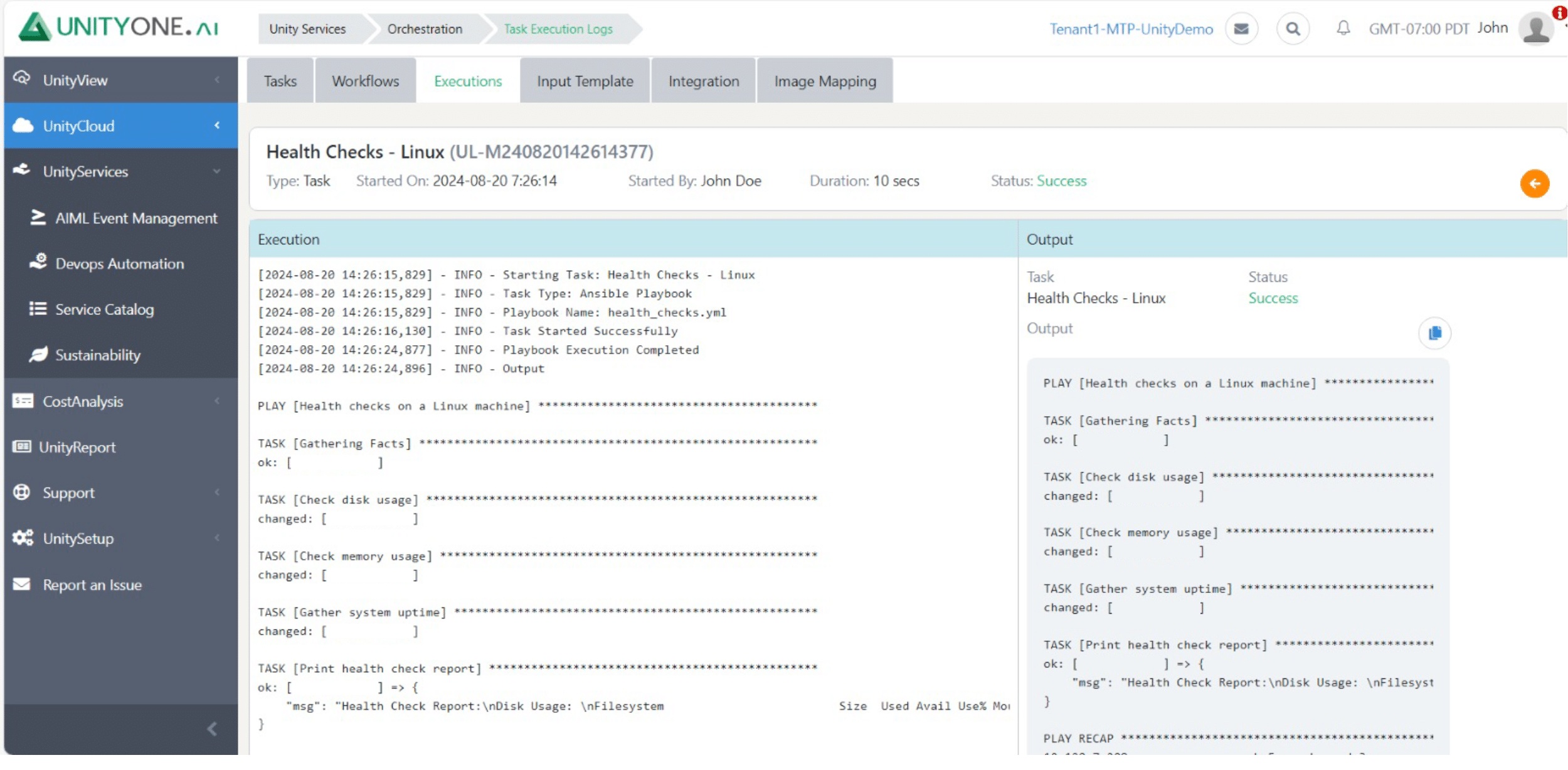
Health Checks
Infrequent health checks can result in undetected problems that escalate into significant outages, affecting business continuity.
Performing regular health checks assesses the overall status of Linux/Unix systems, identifying potential issues before they impact operations.
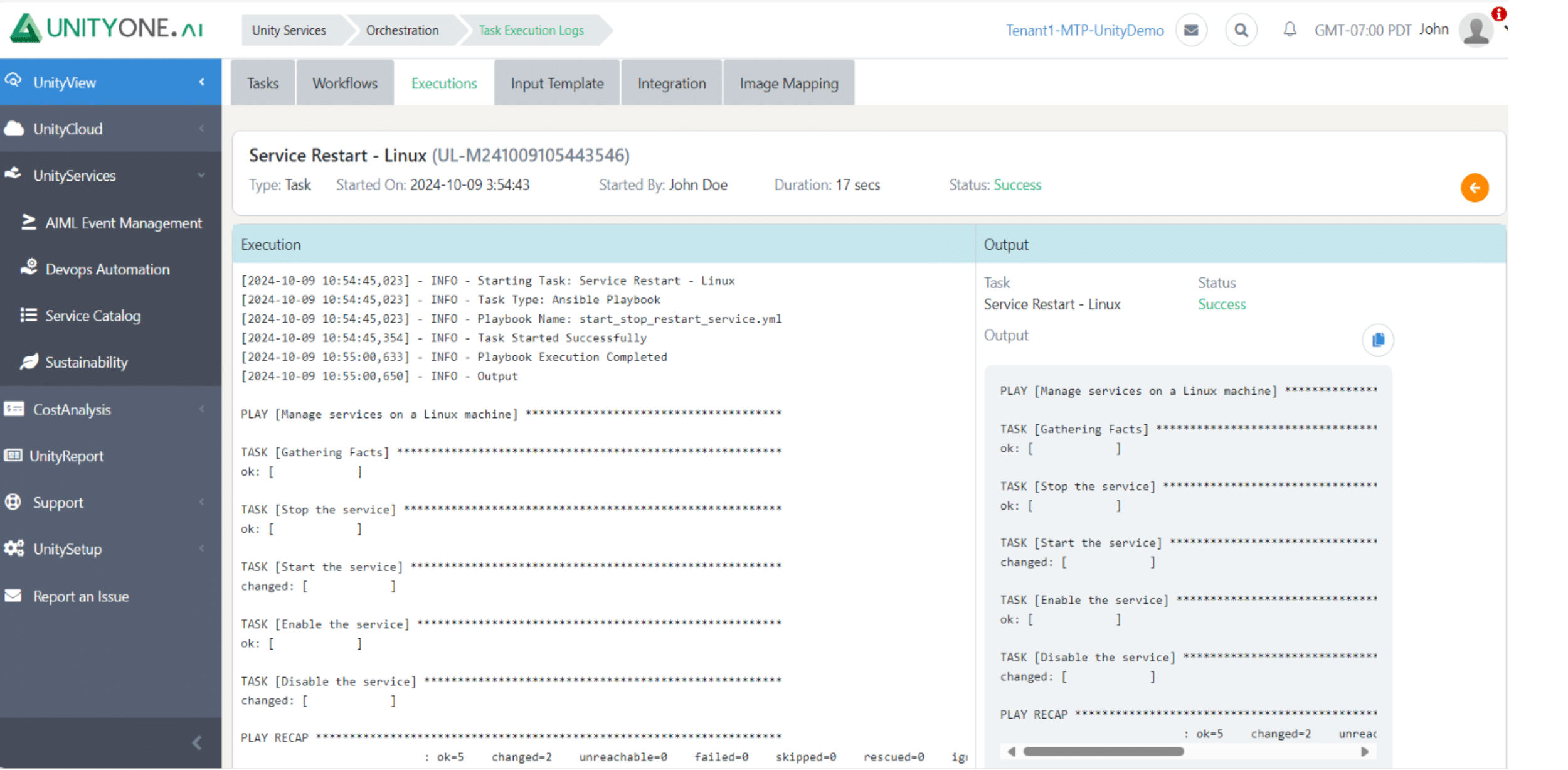
Service Restart
Failure to properly manage service restarts can lead to extended downtime and disruptions in service availability, negatively impacting users and operations.
Restarting services allows for the application of updates or configuration changes, ensuring systems run smoothly and efficiently.
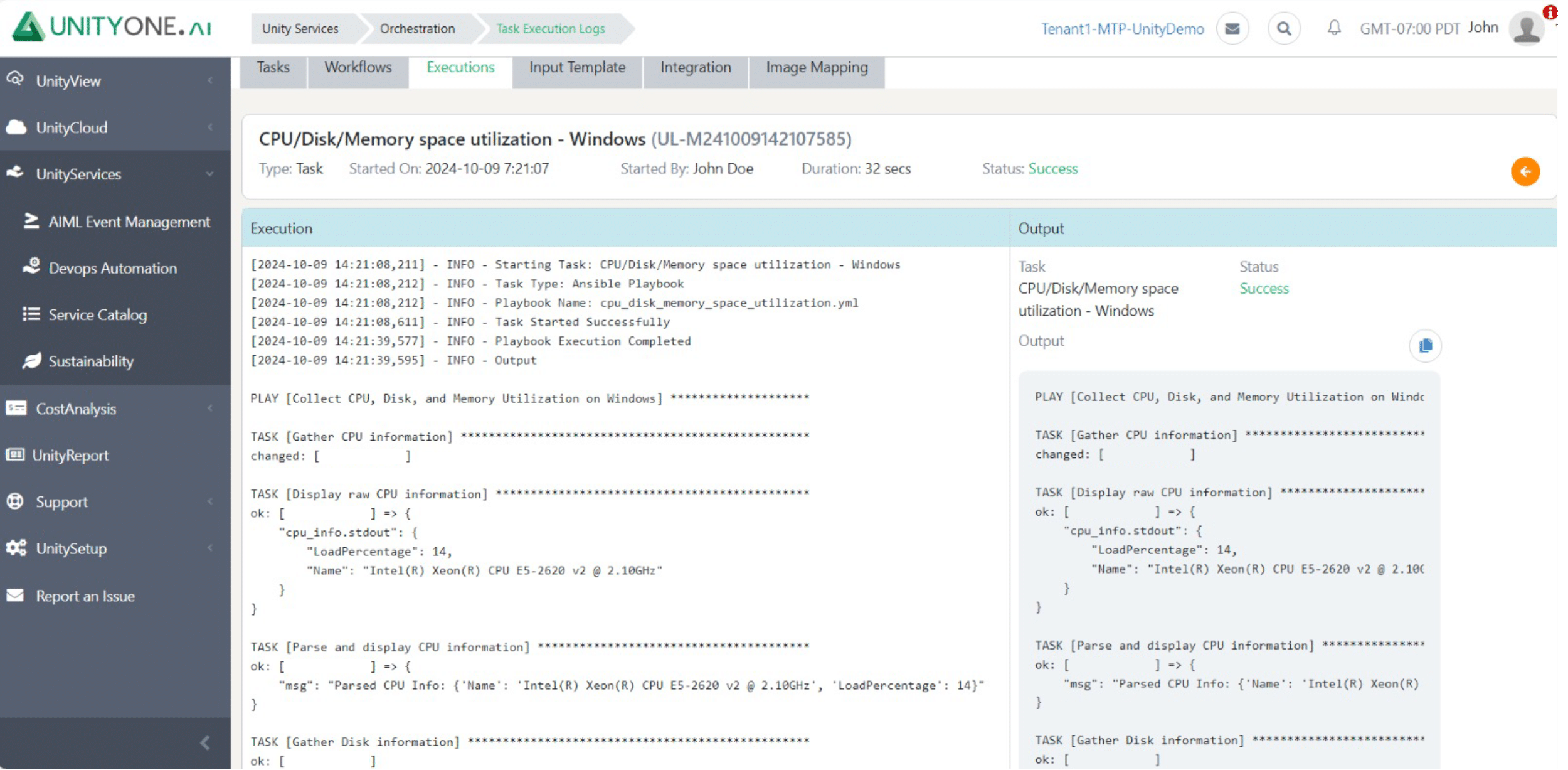
CPU/Disk/Memory Utilization
Infrequent health checks can result in undetected problems that escalate into significant outages, affecting business continuity.
Performing regular health checks assesses the overall status of Linux/Unix systems, identifying potential issues before they impact operations.
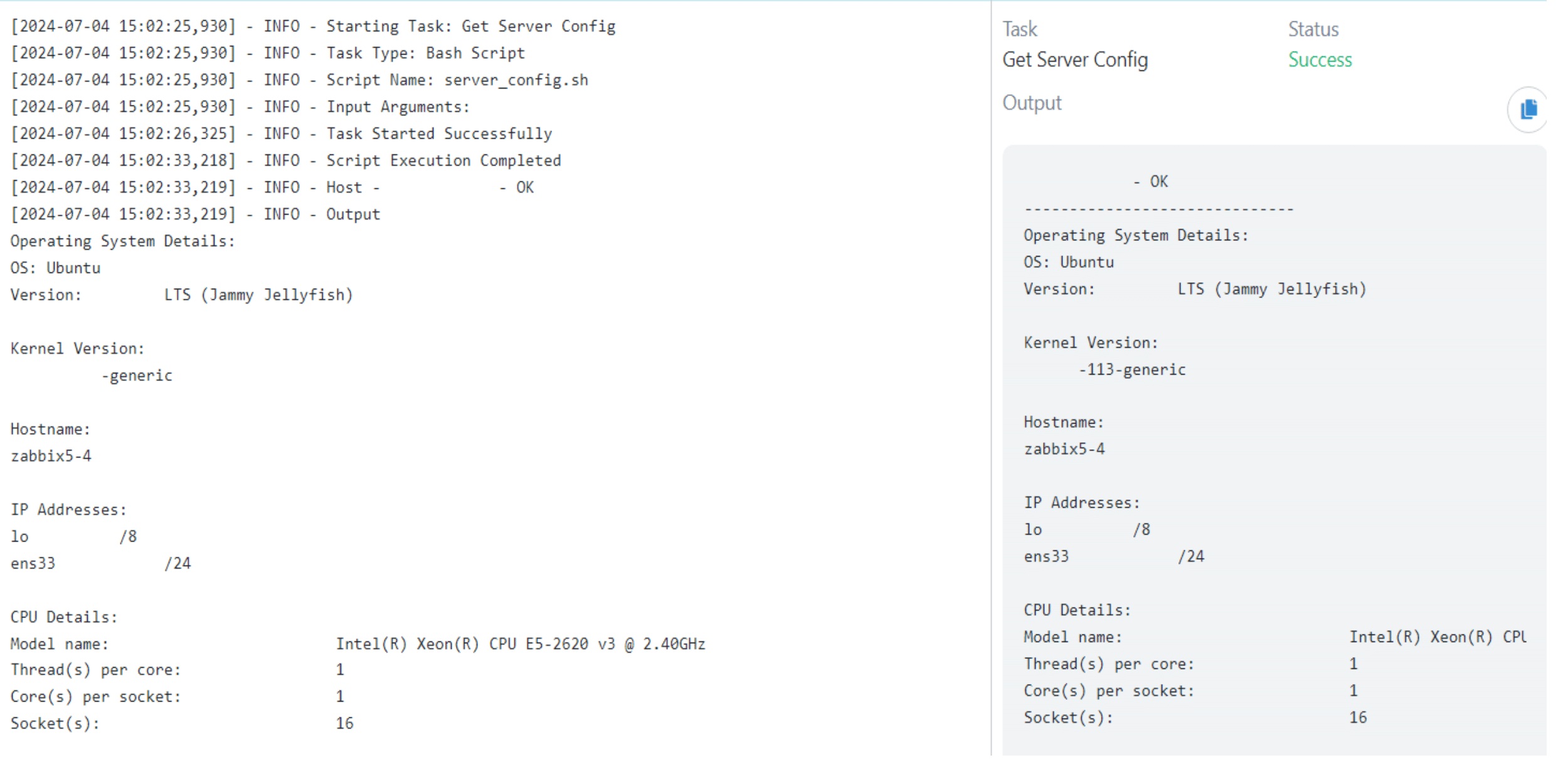
Get Server Configuration
Lack of accessible configuration information can complicate troubleshooting efforts, resulting in prolonged downtime and operational inefficiencies.
Retrieving server configuration details provides insights into system settings and enables effective management and troubleshooting.
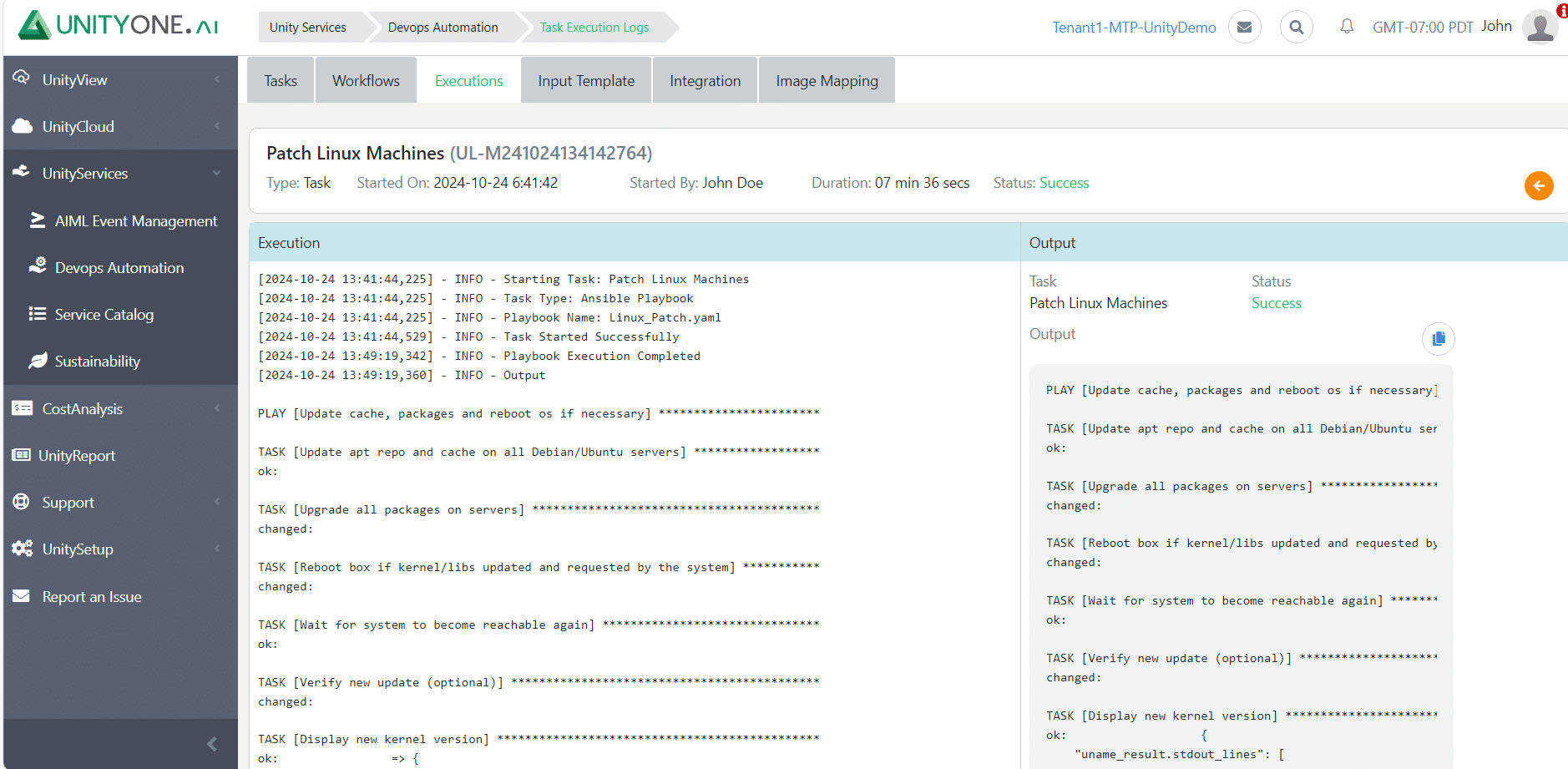
Patch Linux Machines
Applying patches to Linux systems ensures that security vulnerabilities and bugs are addressed promptly, maintaining system integrity and performance.
Applying patches to Linux systems ensures that security vulnerabilities and bugs are addressed promptly, maintaining system integrity and performance.
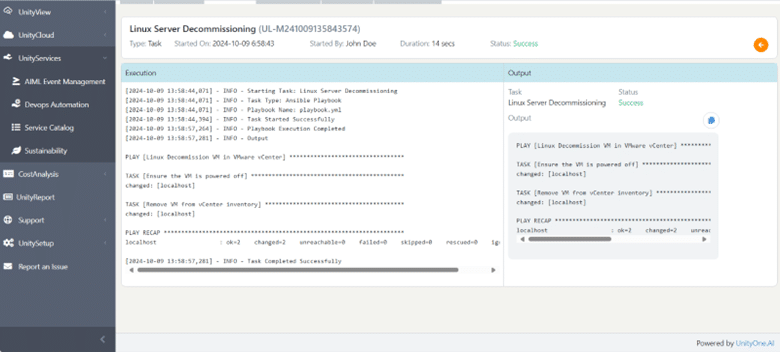
Linux Service Decommissioning
Failure to properly decommission services can lead to unnecessary resource consumption and increased vulnerability, complicating system management.
Safely decommissioning unused Linux services prevents resource wastage and reduces the attack surface for potential security threats.
Health Check
File System Full
Service Restart
CPU/Disk/Memory Utilization
Health Check
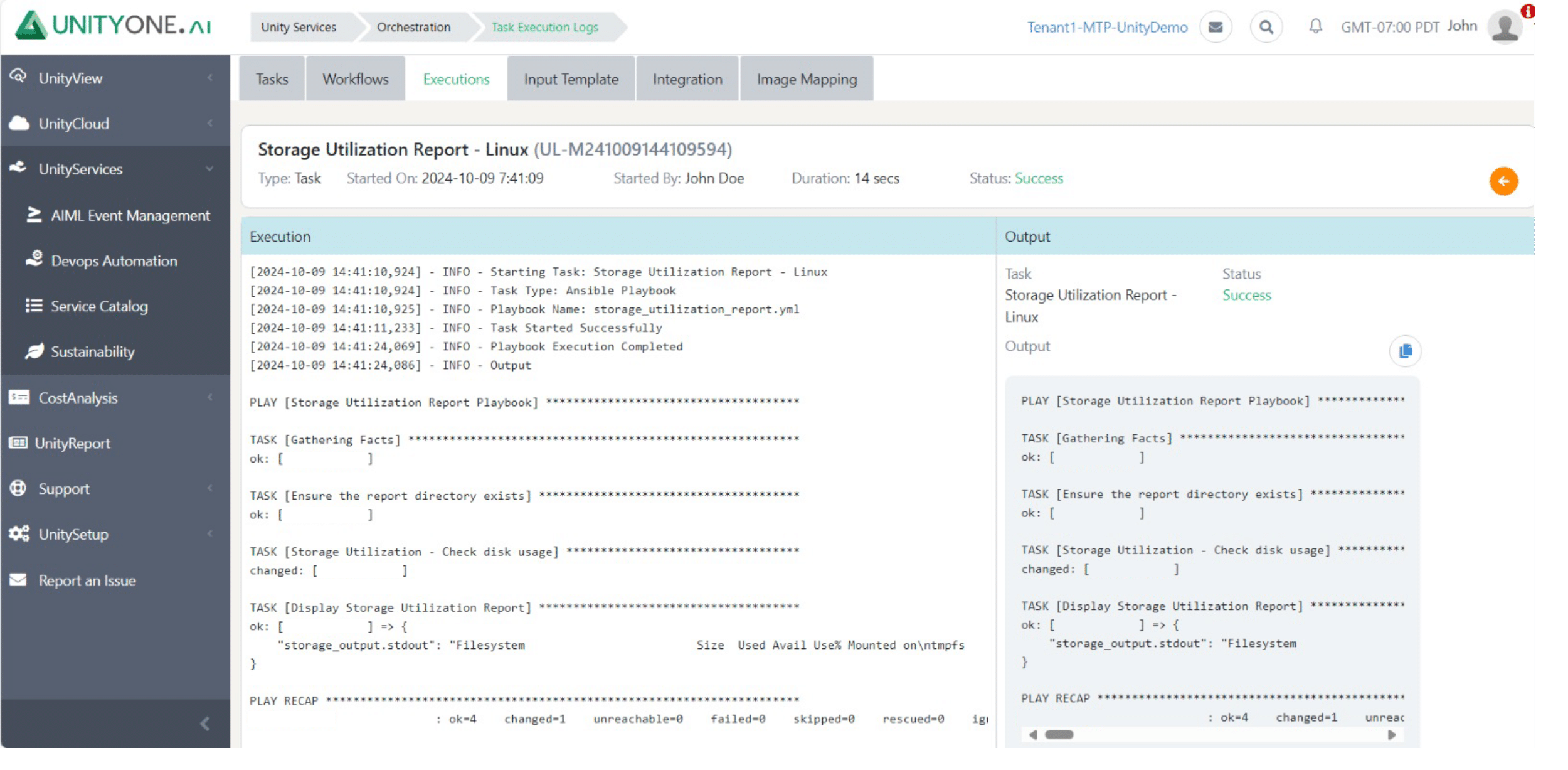
Storage Utilization
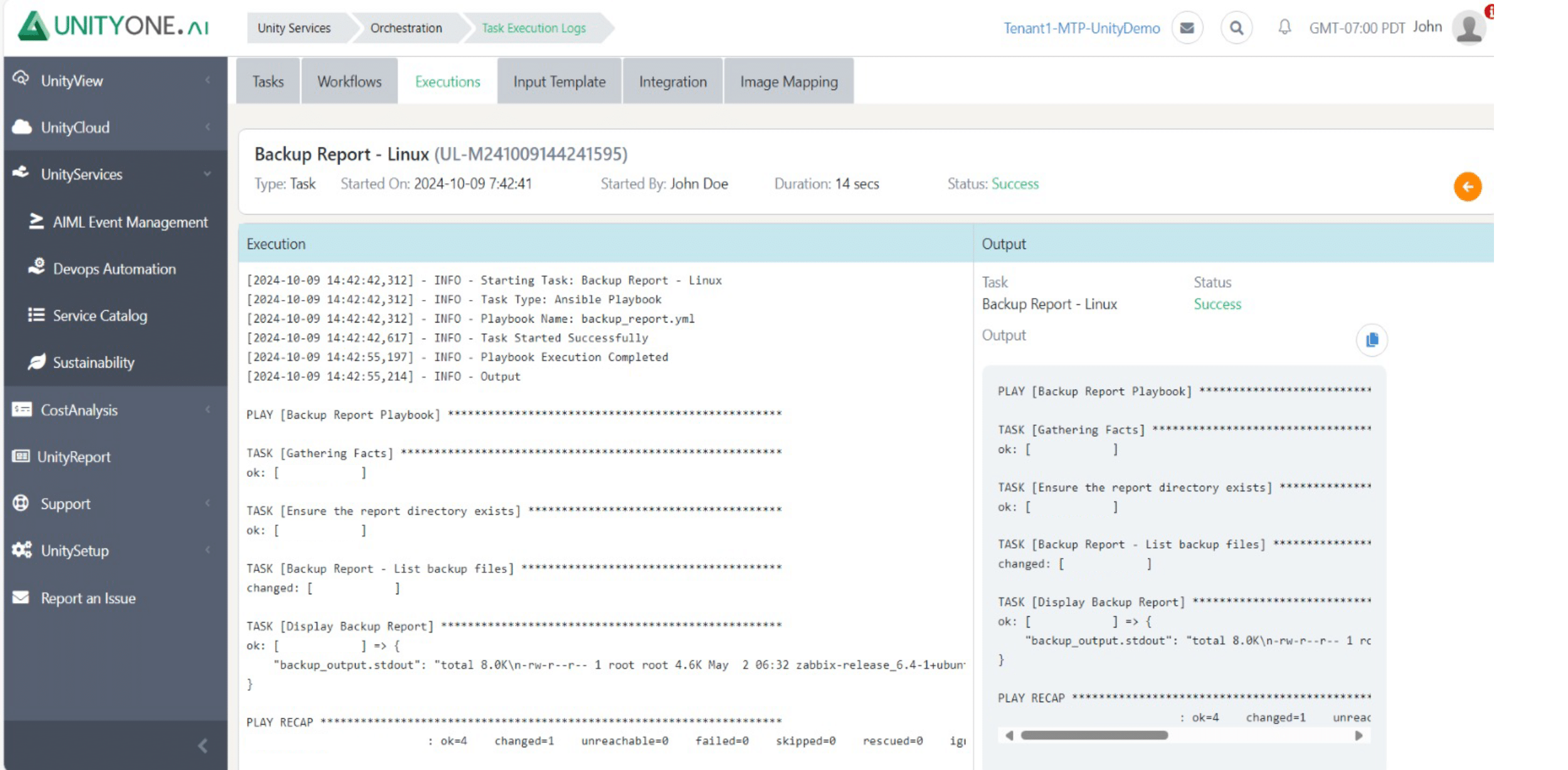
Backup Report
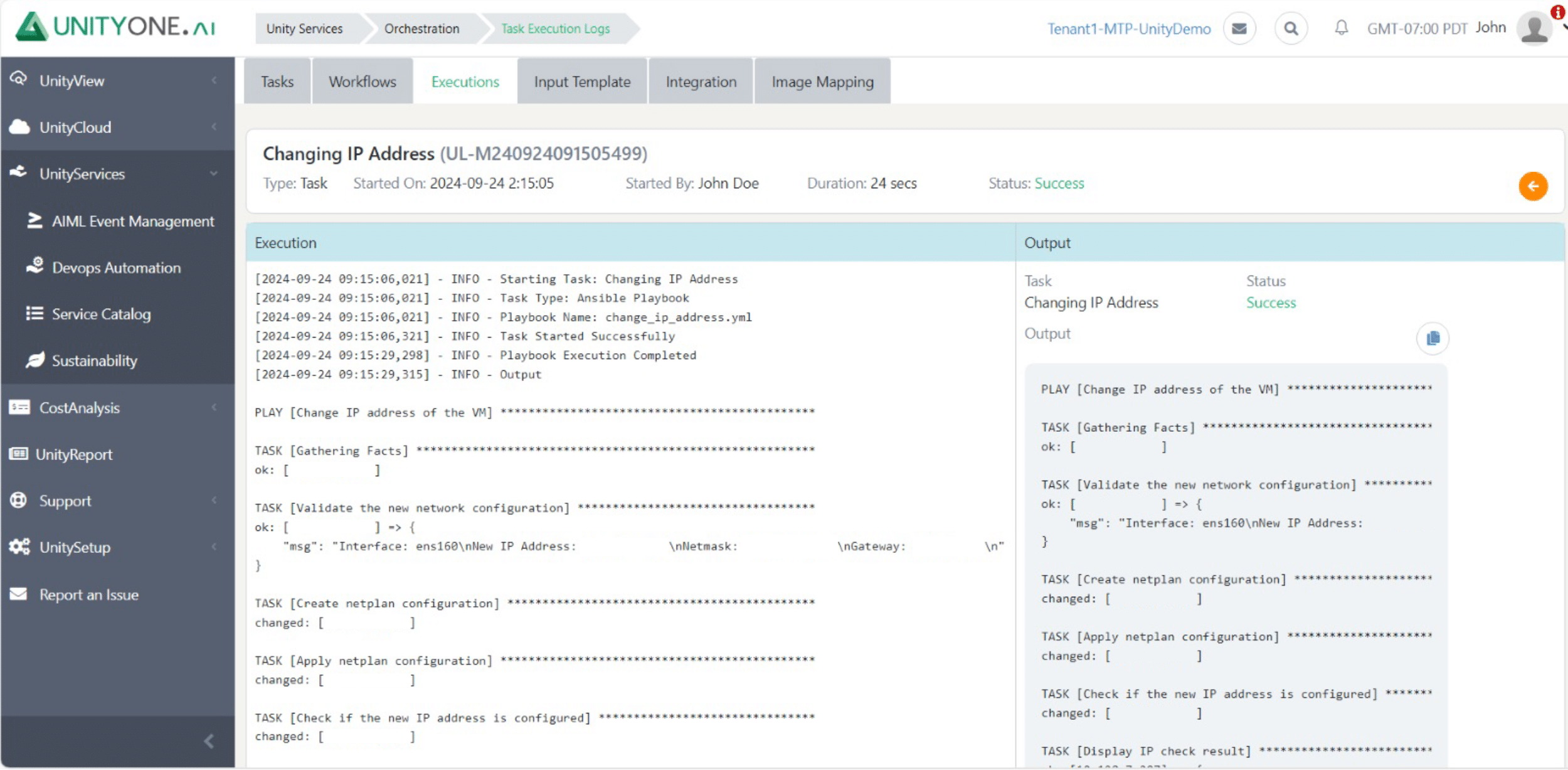
Changing IP Address
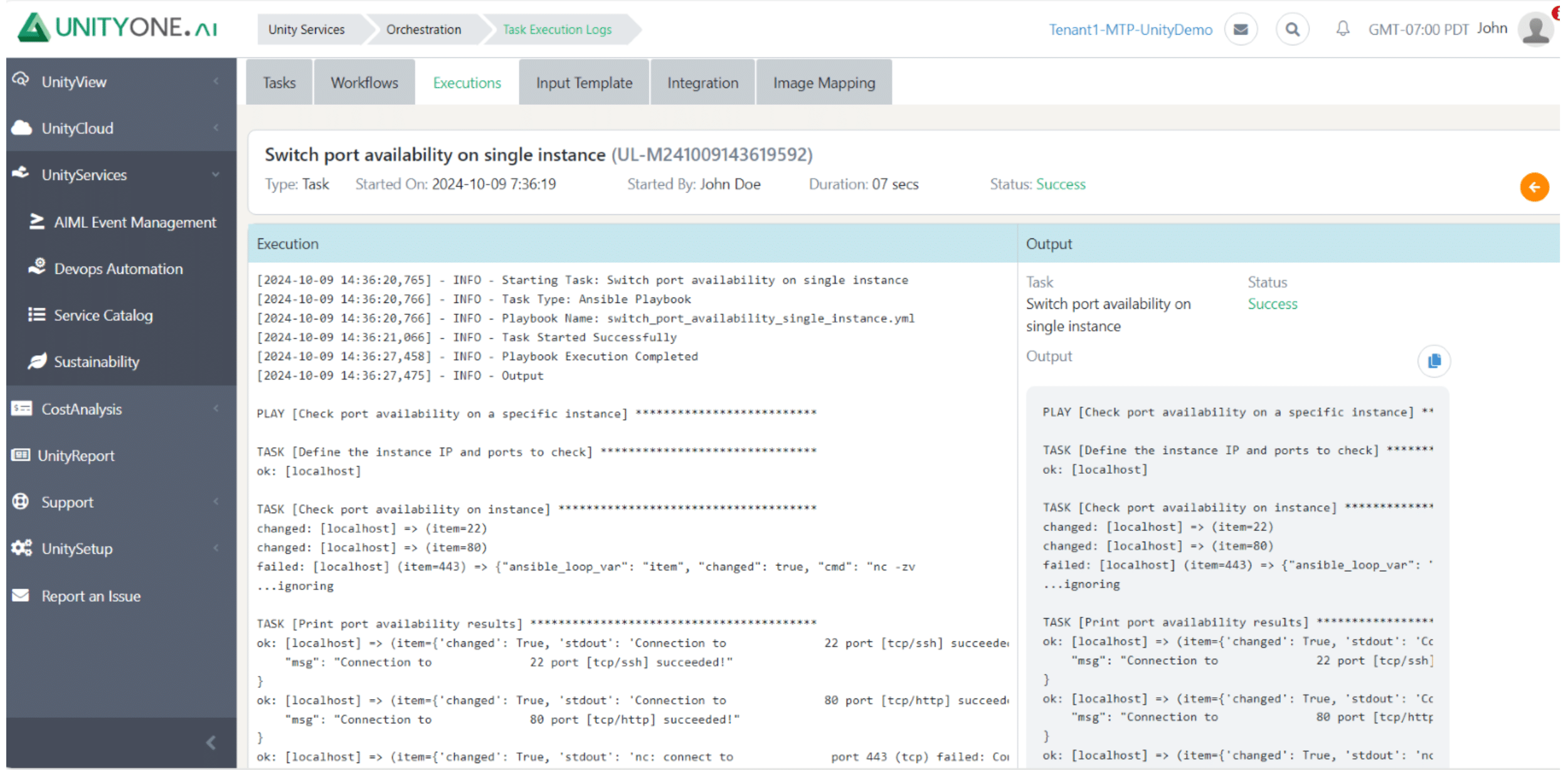
Switch Port Availability on Single Instance
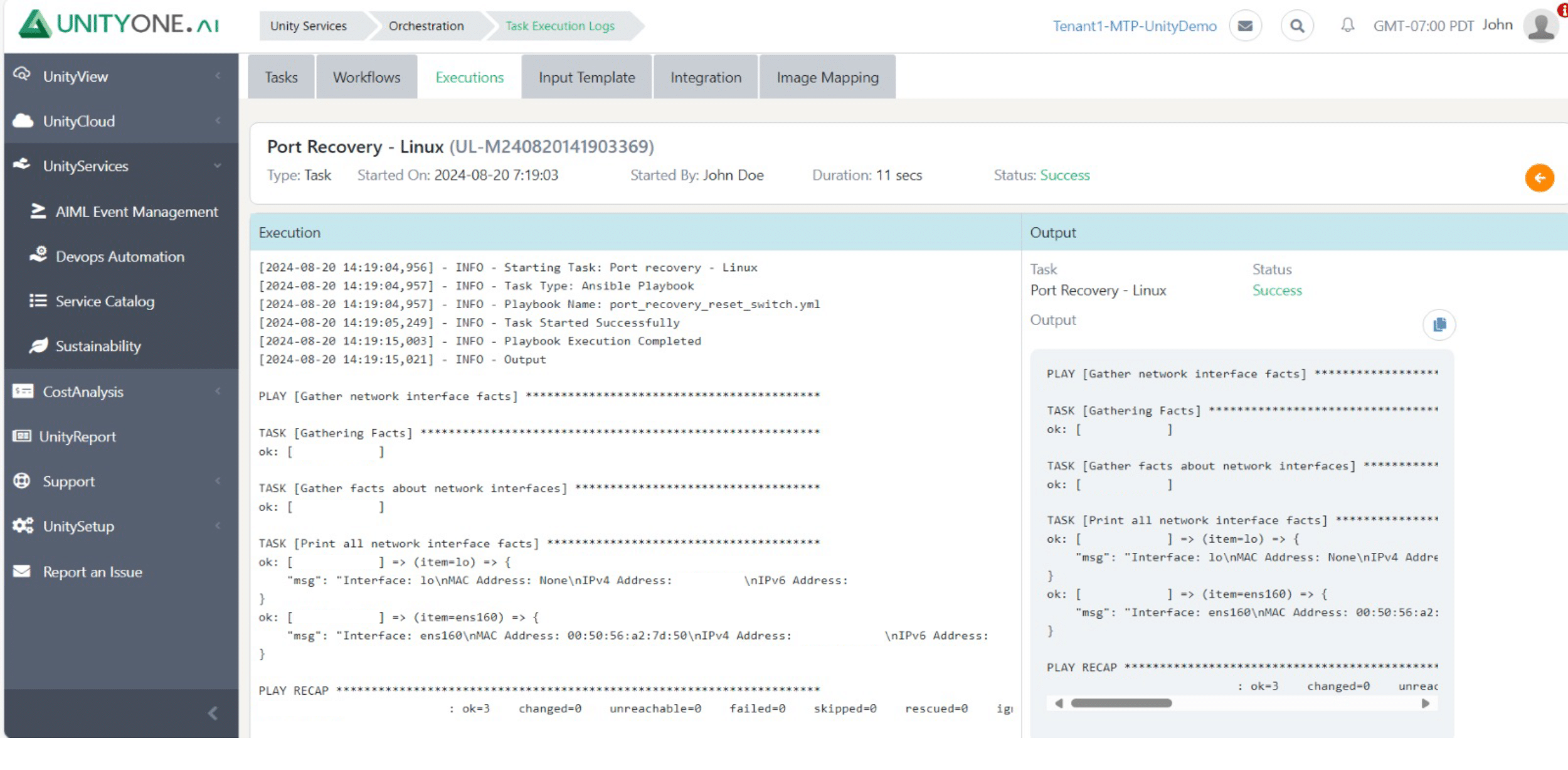
Port Recovery
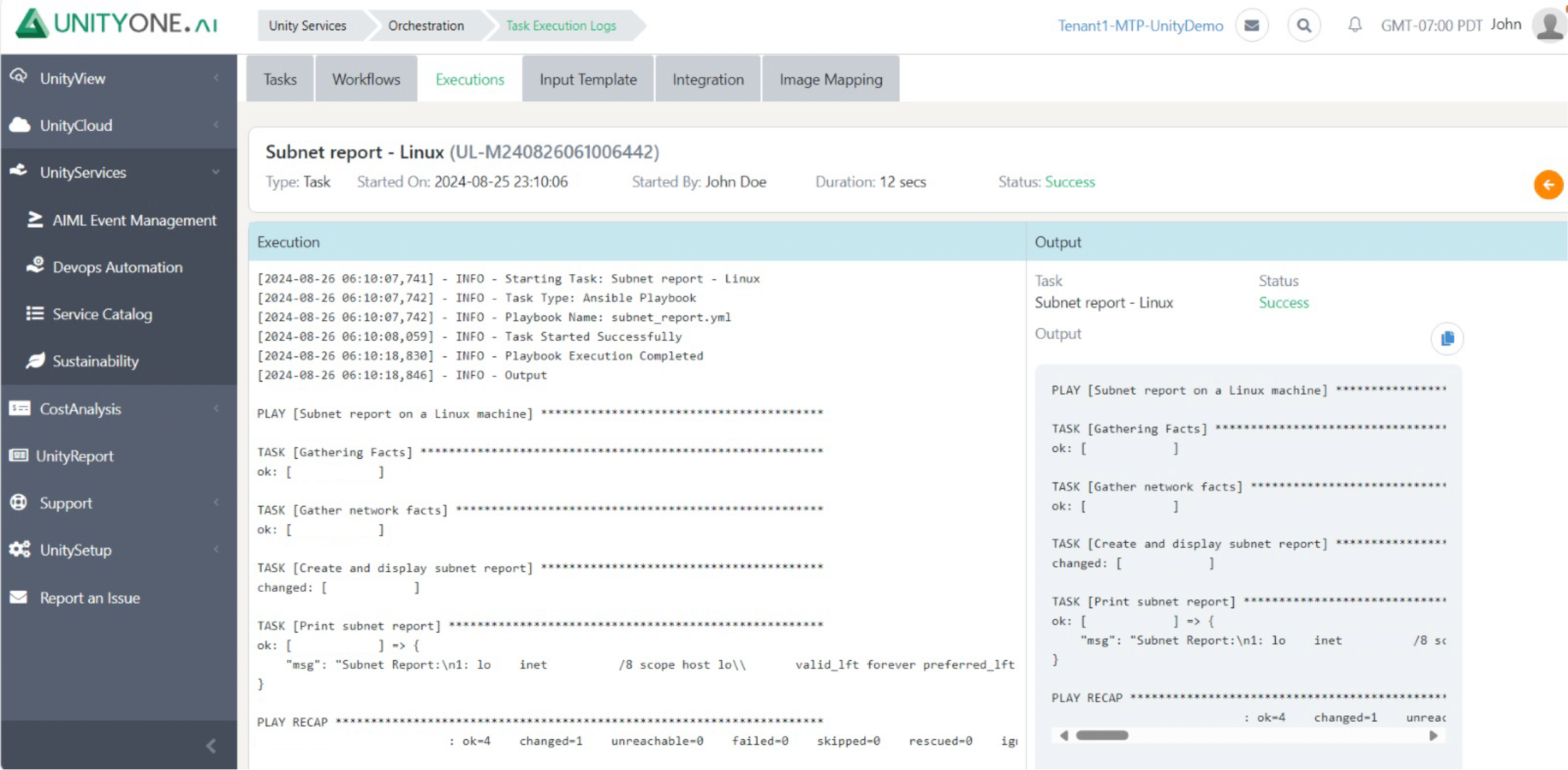
Subnet Report
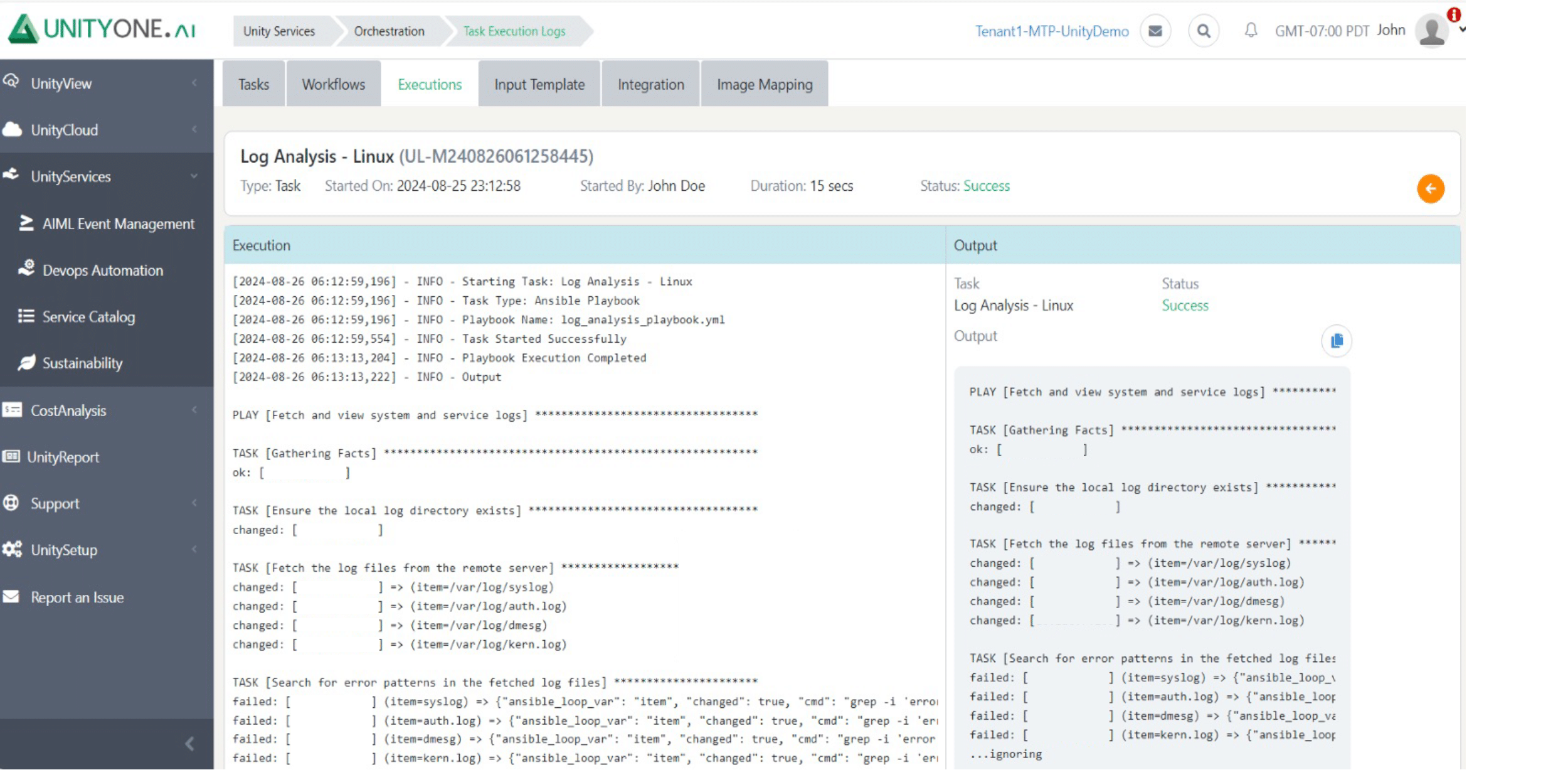
Log Analysis
Health Checks
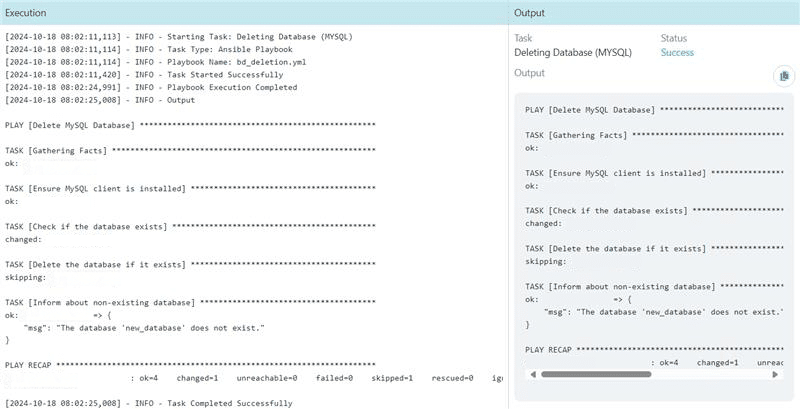
Deleting Database
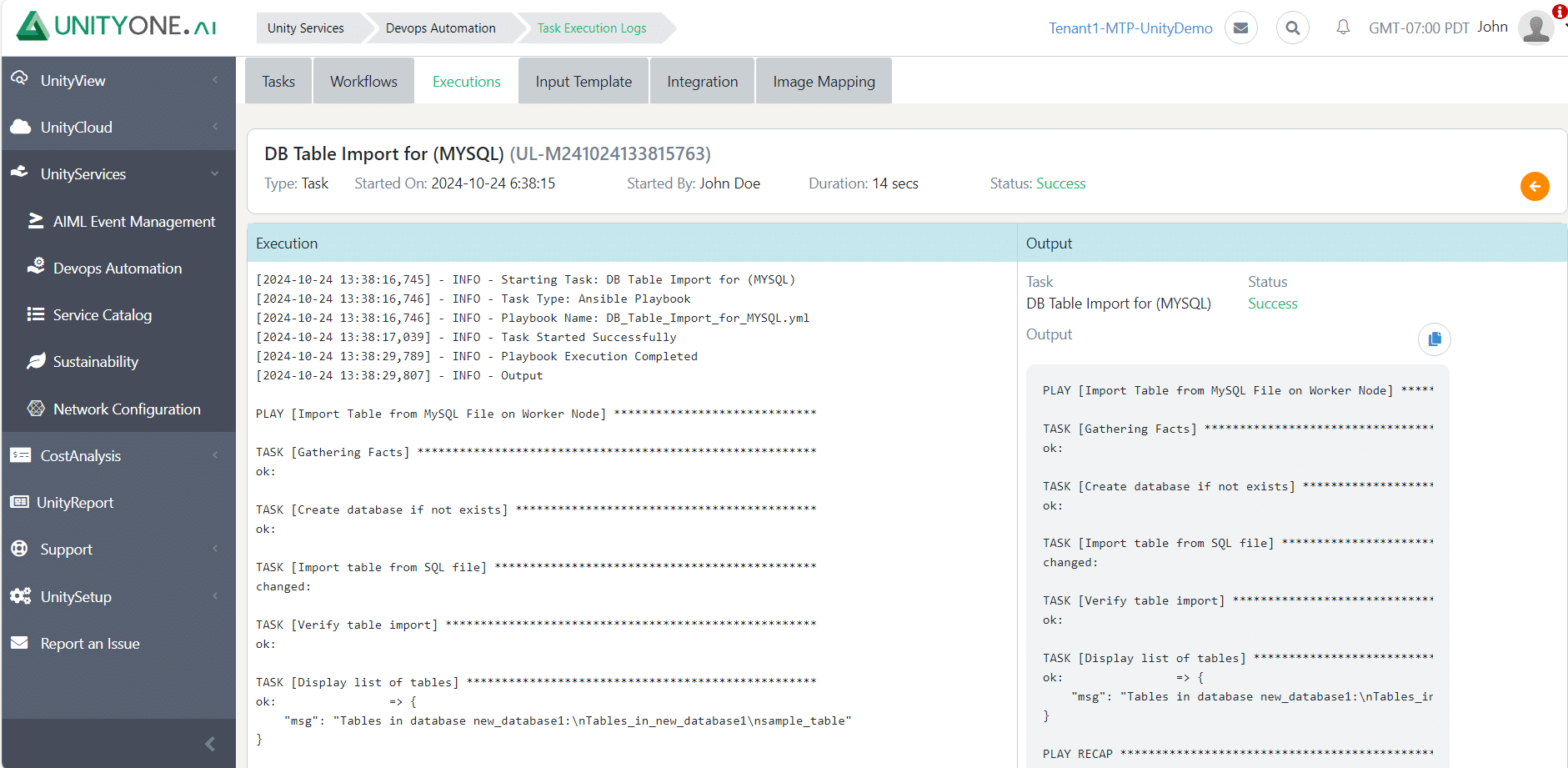
DB Table Import – MySQL
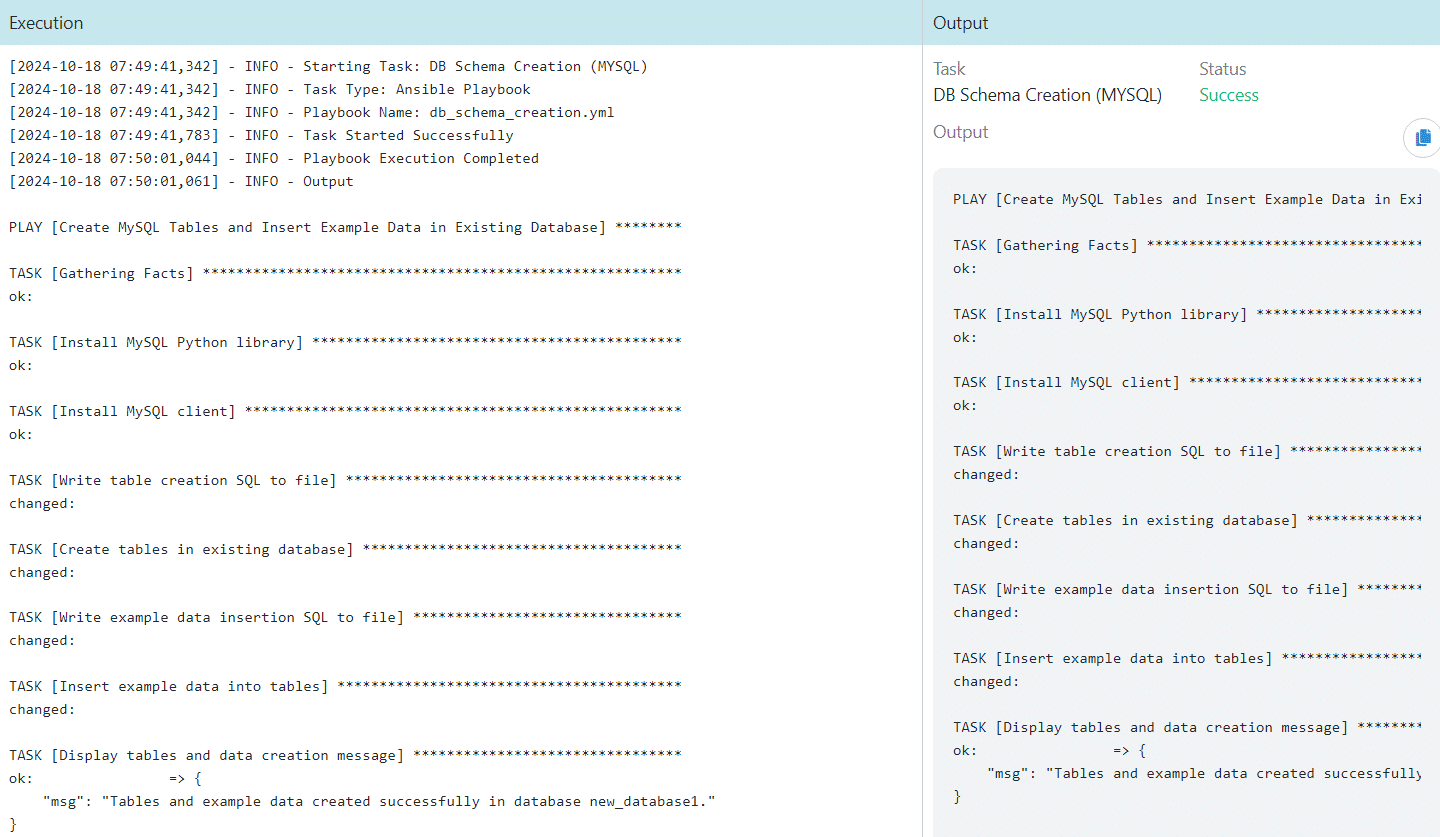
DB Schema Creation – MySQL
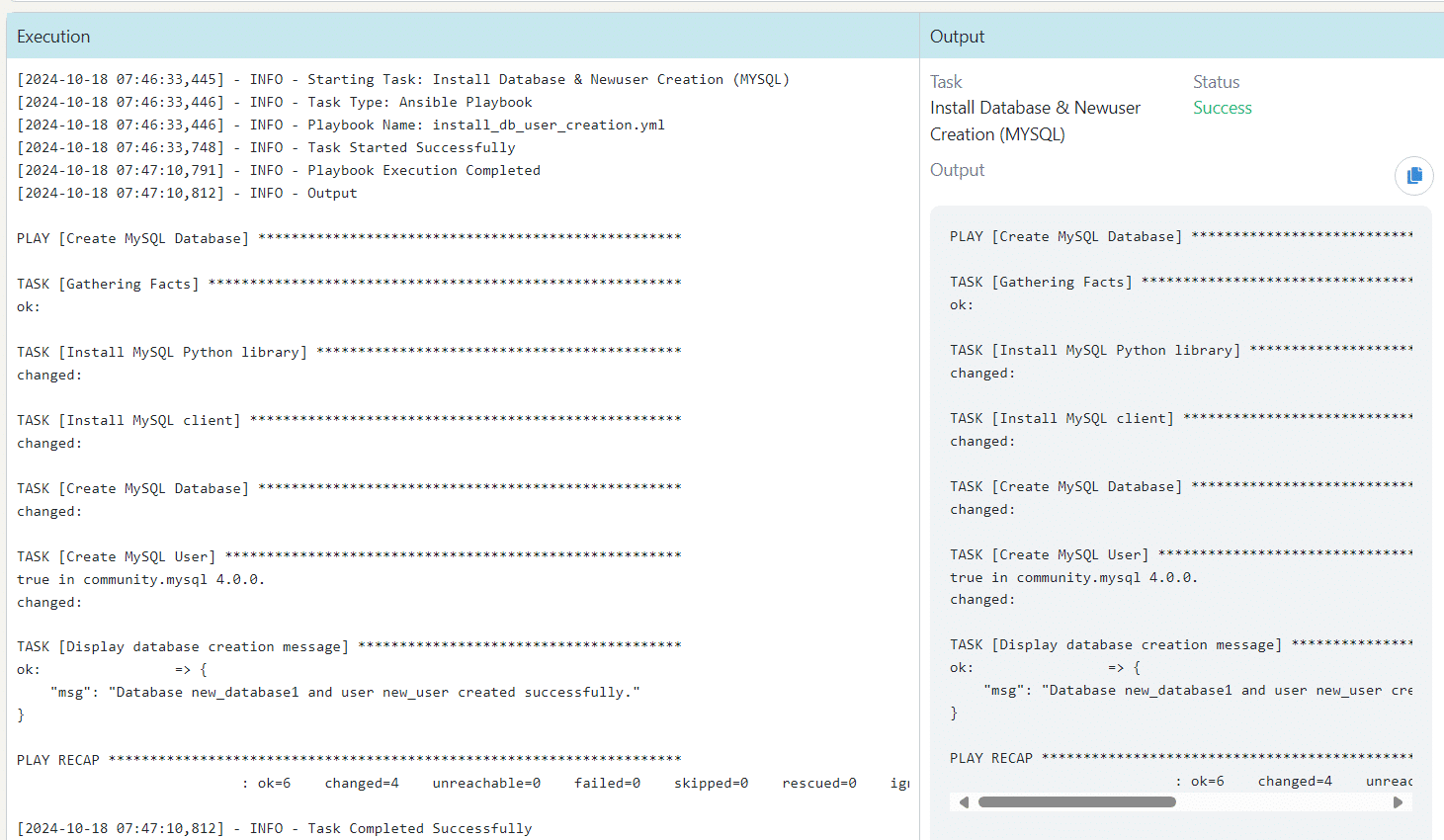
Install Database and New User Creation – MySQL
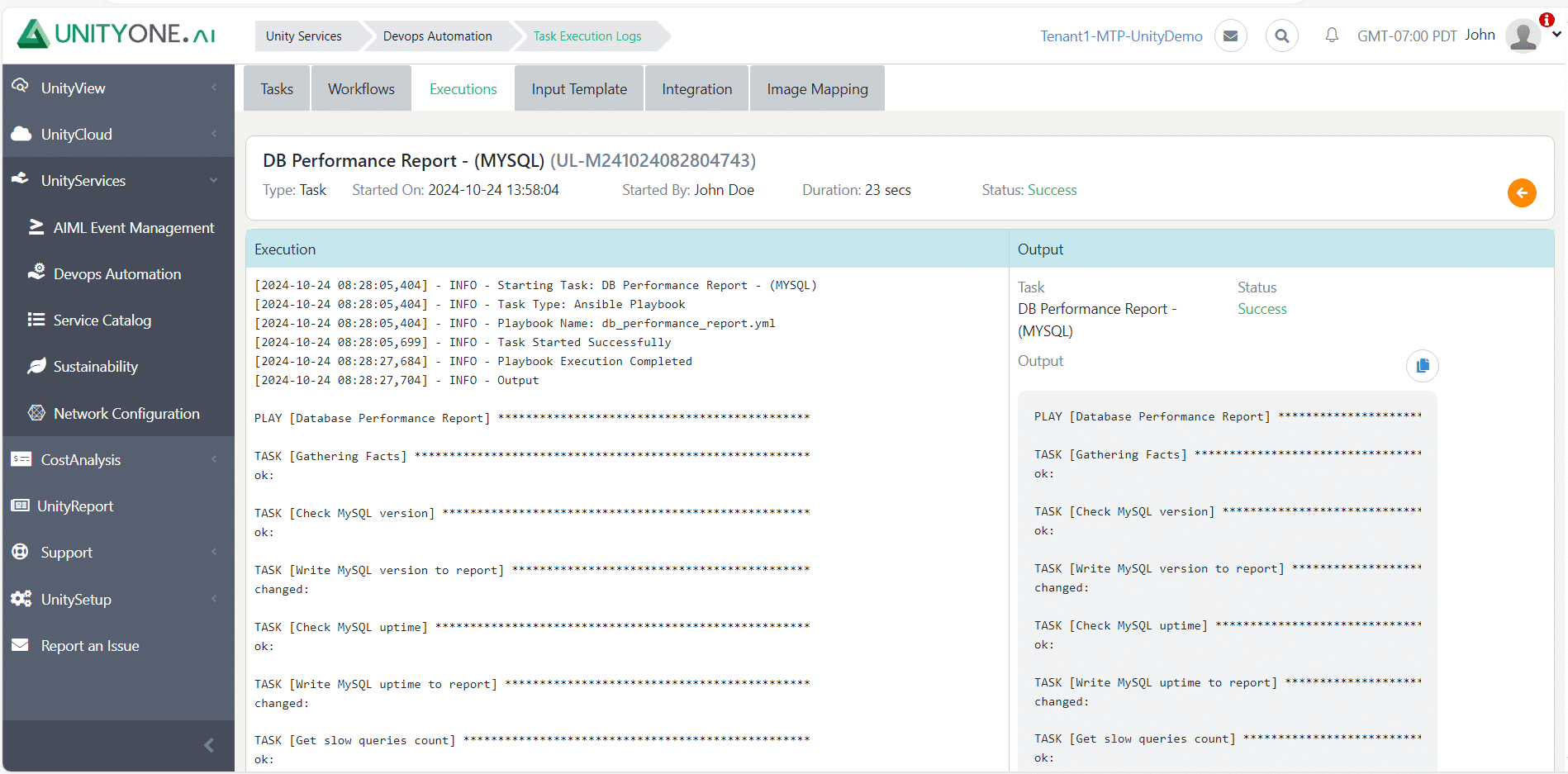
DB Performance Report – MySQL
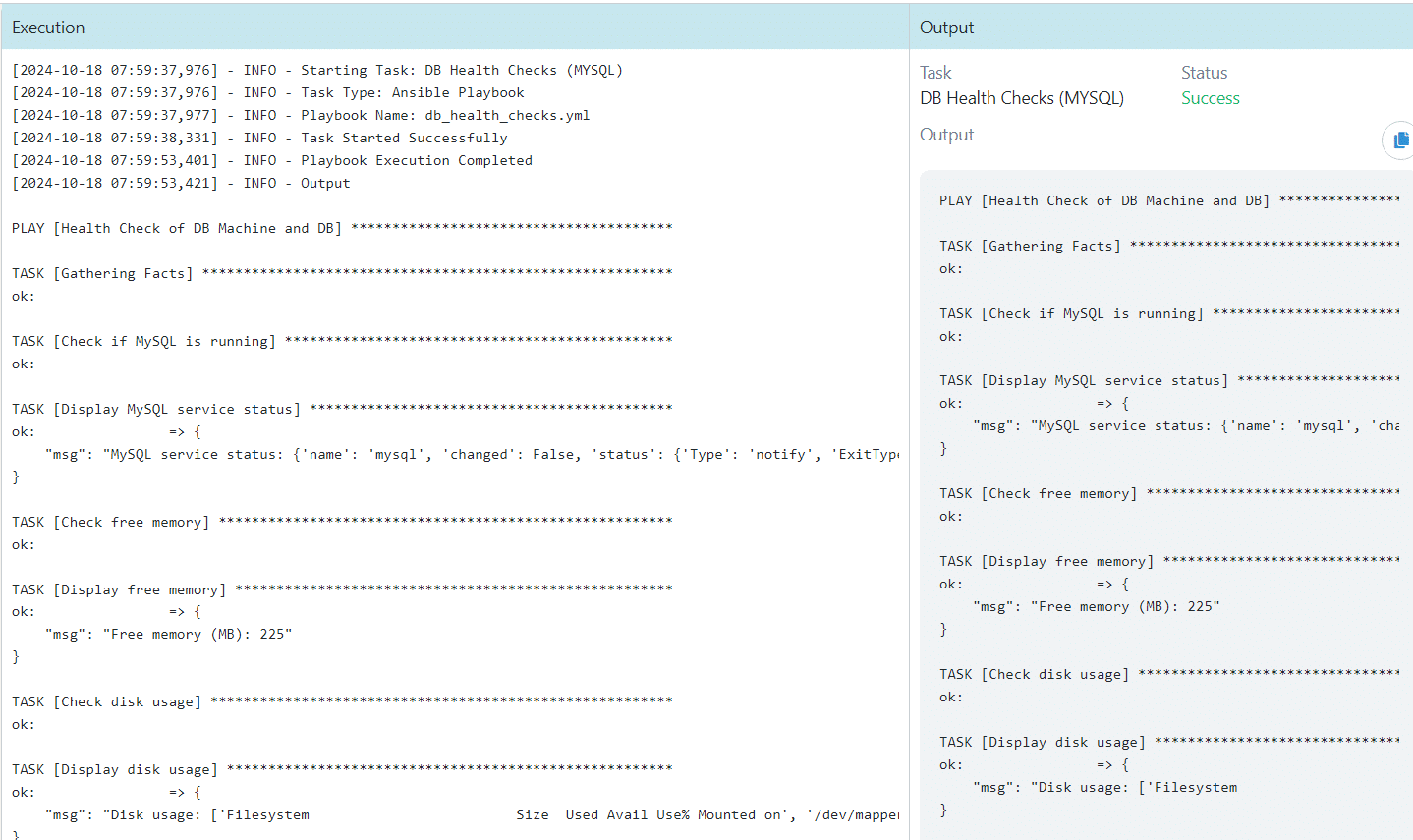
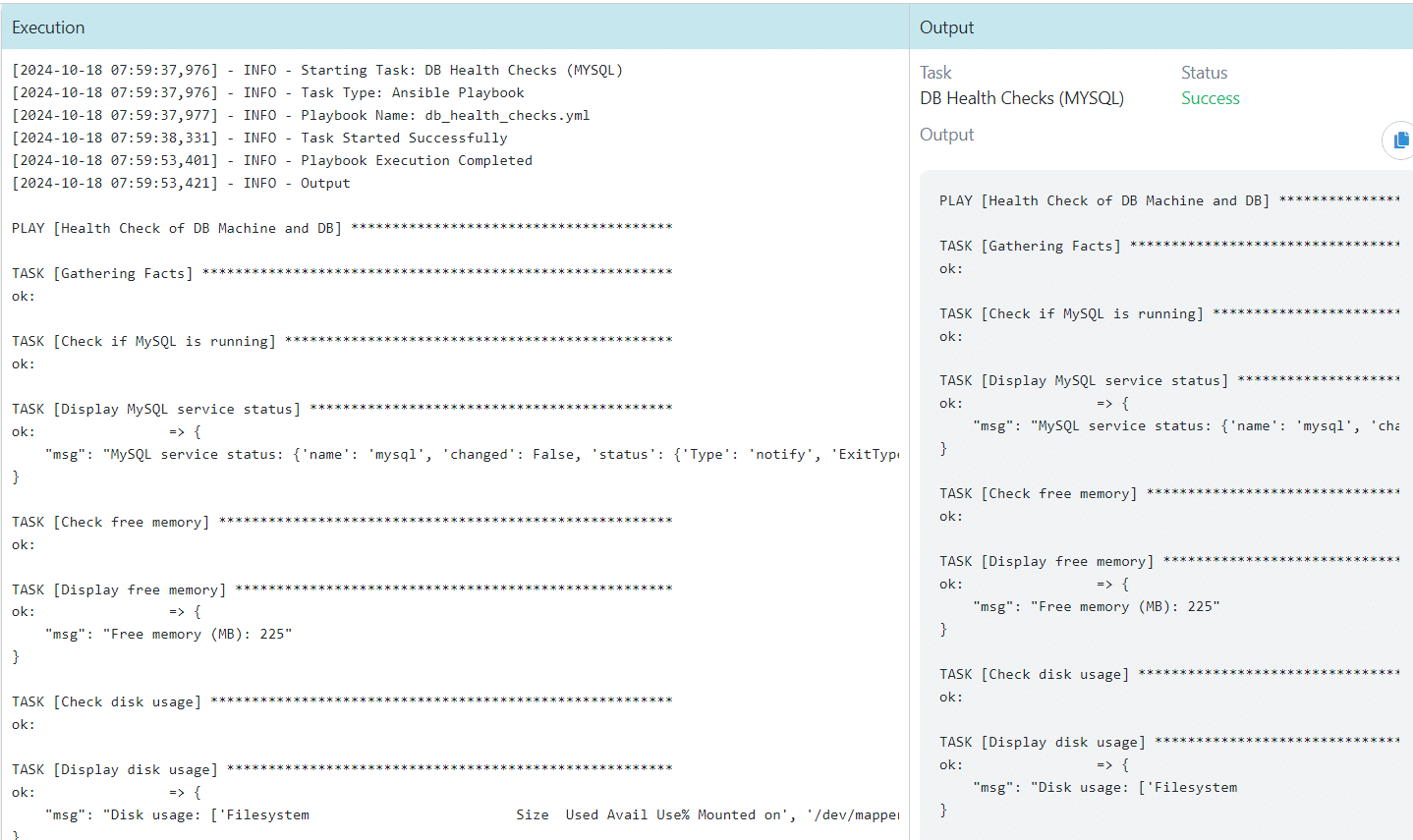
DB Health Checks – MySQL
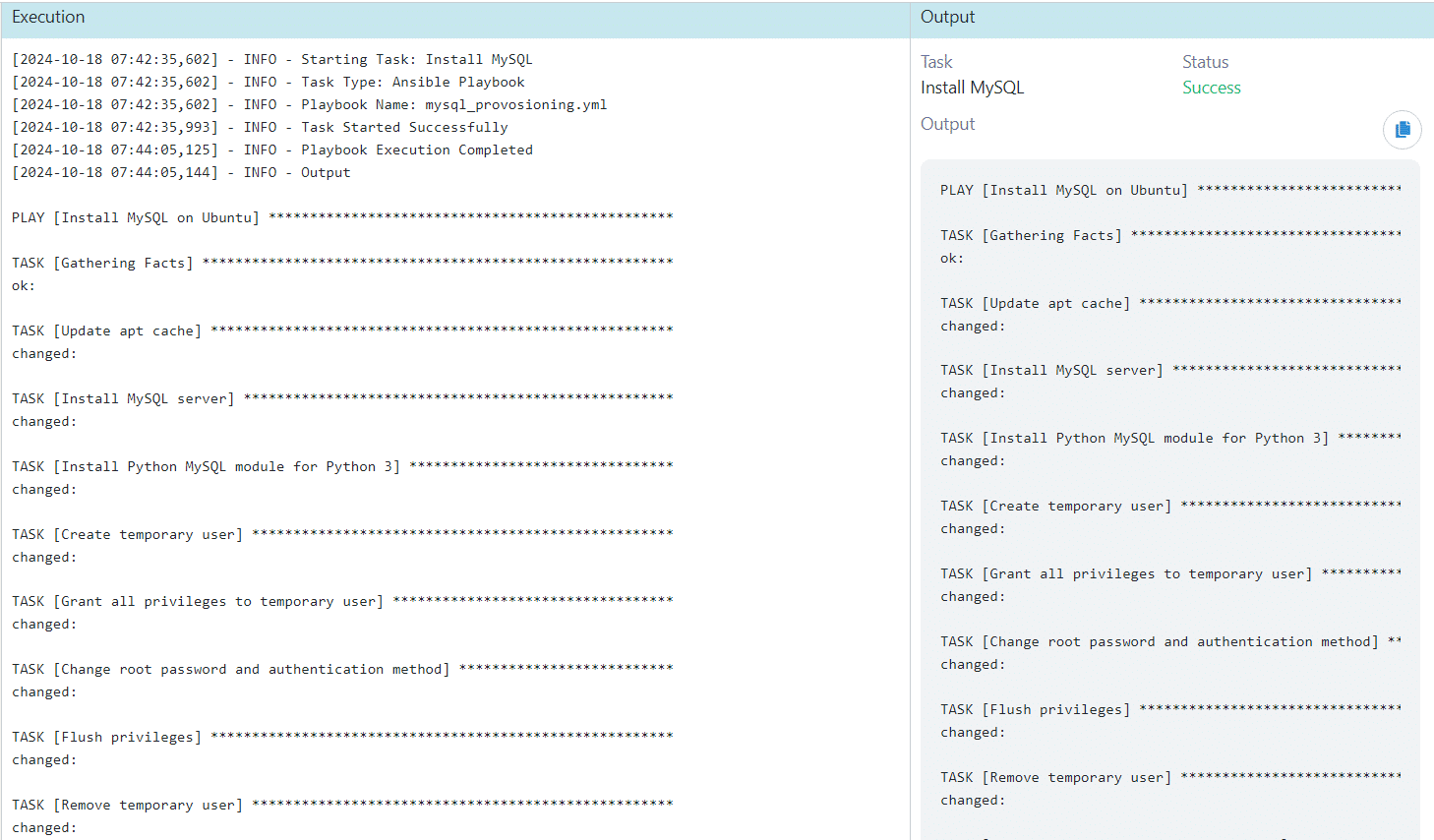
Install MySQL
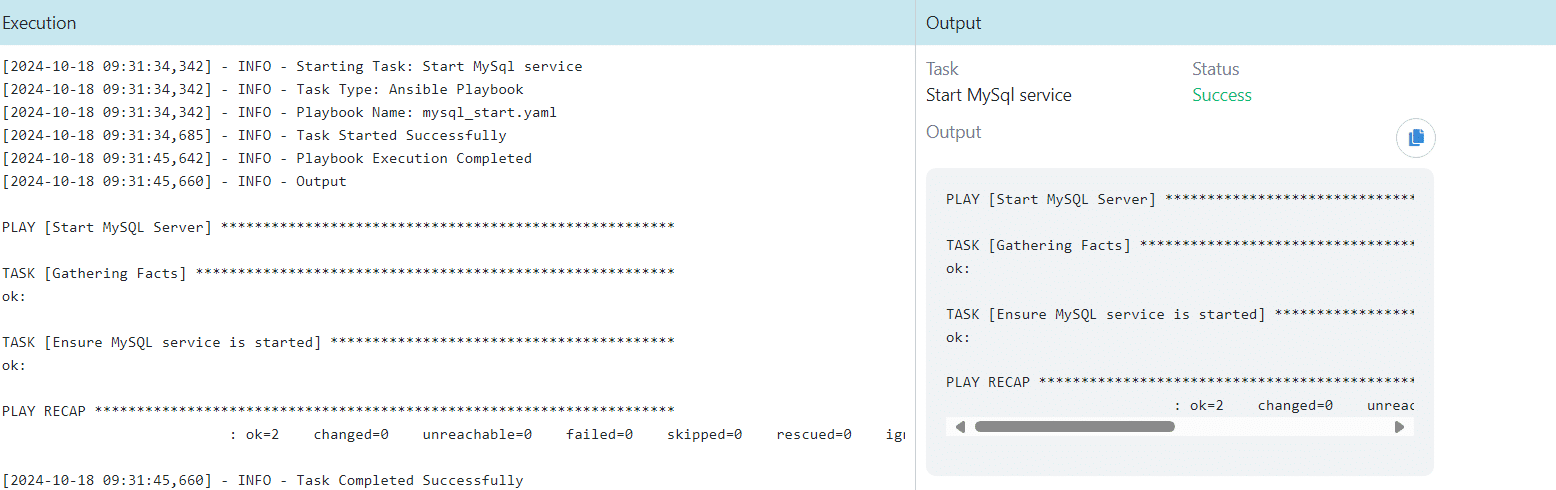
Start MySQL Service
Stop MySQL Service
Uninstall Unity Monitoring Agent
Install Unity Monitoring Agent
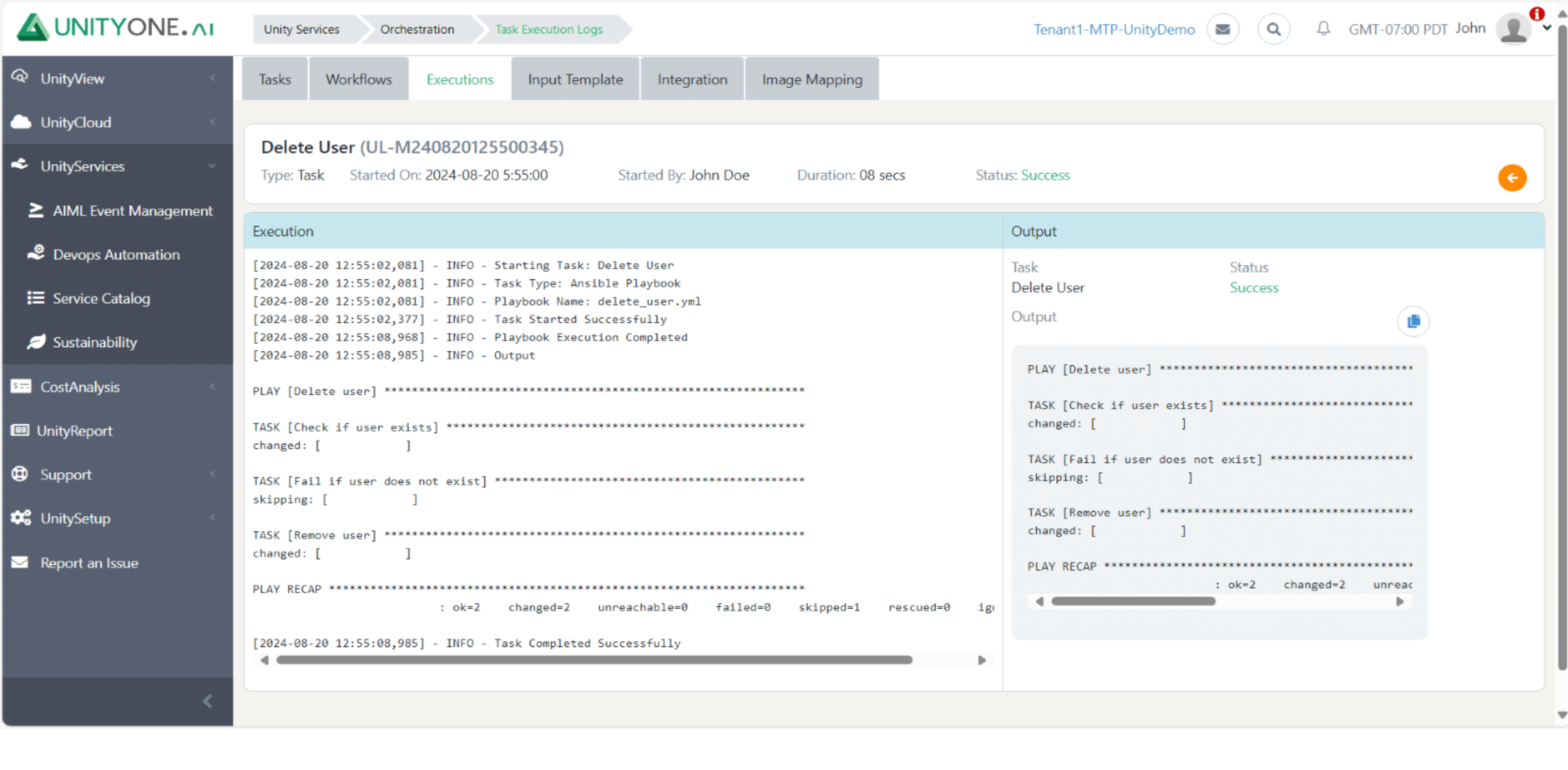
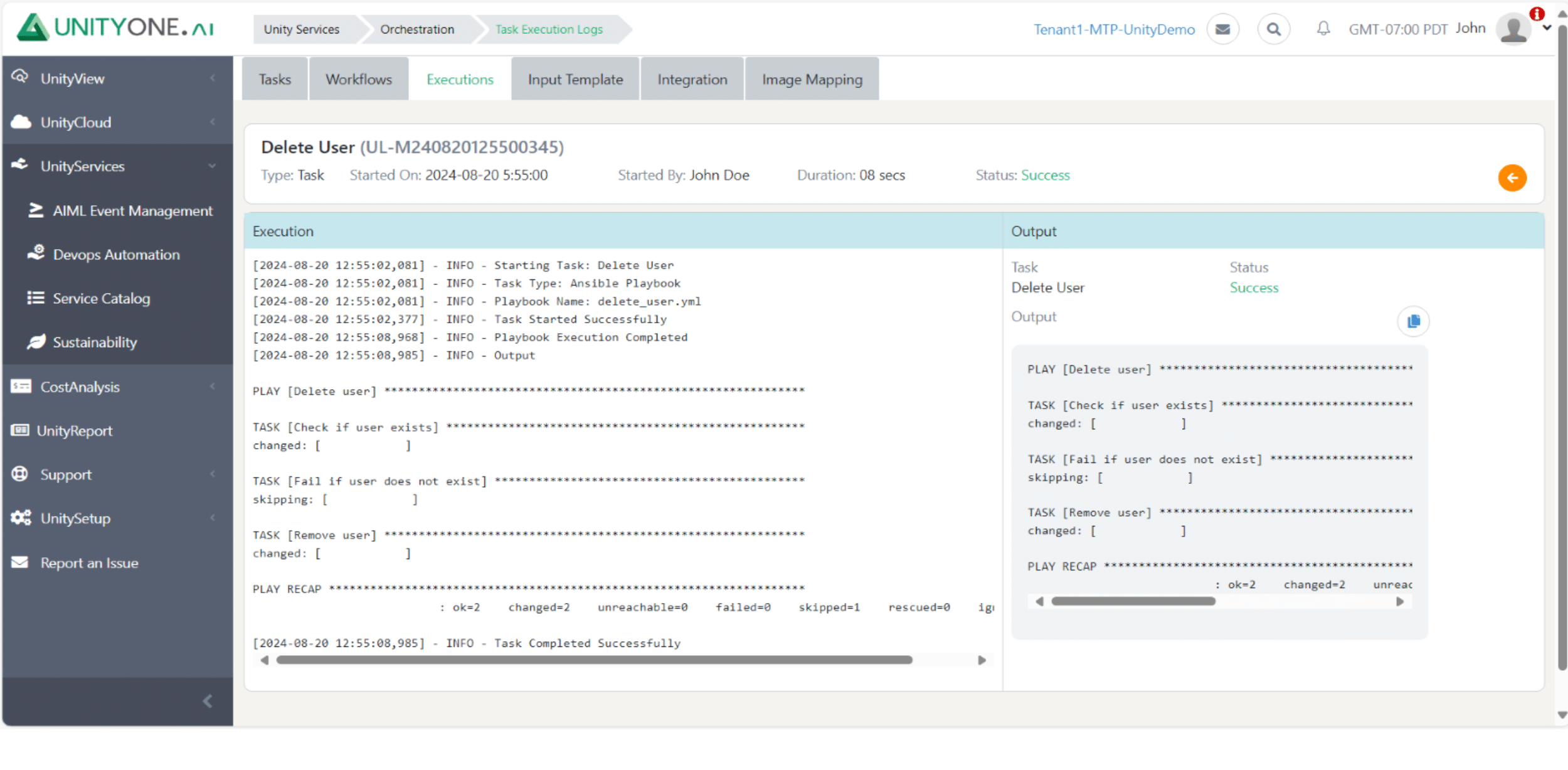
Delete User
Removing user accounts that are no longer needed helps maintain security and user management within Linux/Unix systems.
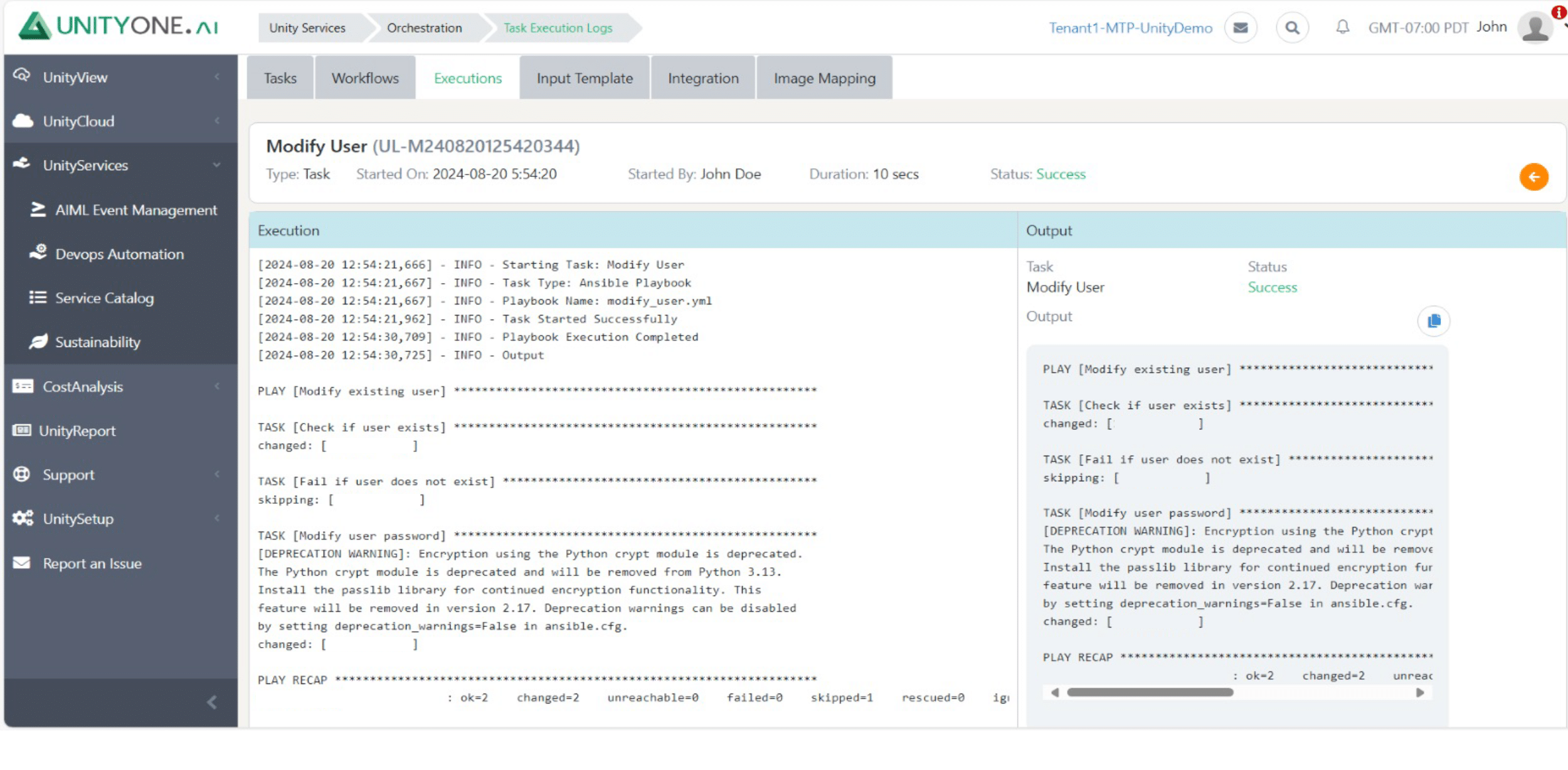
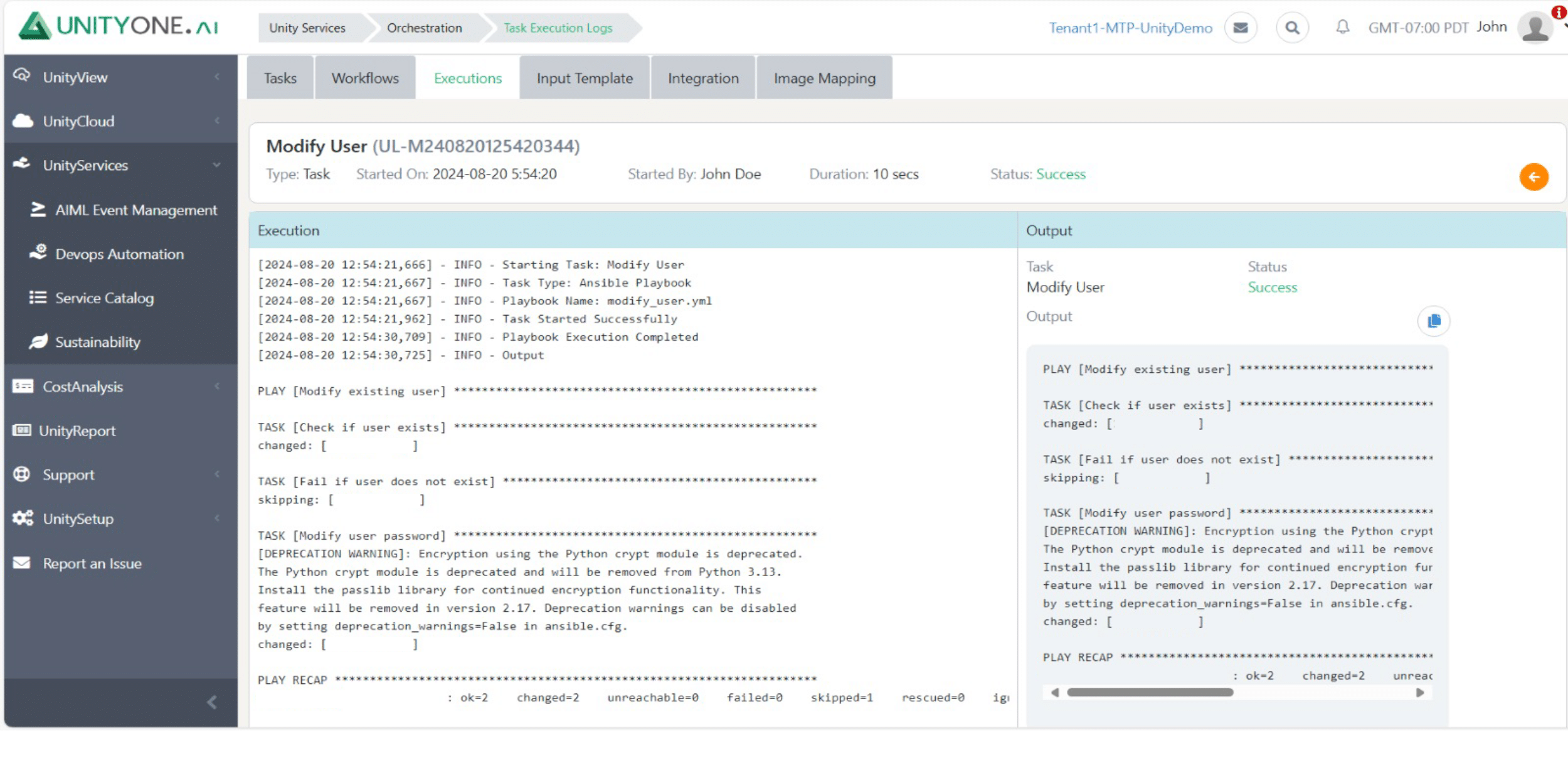
Modify User
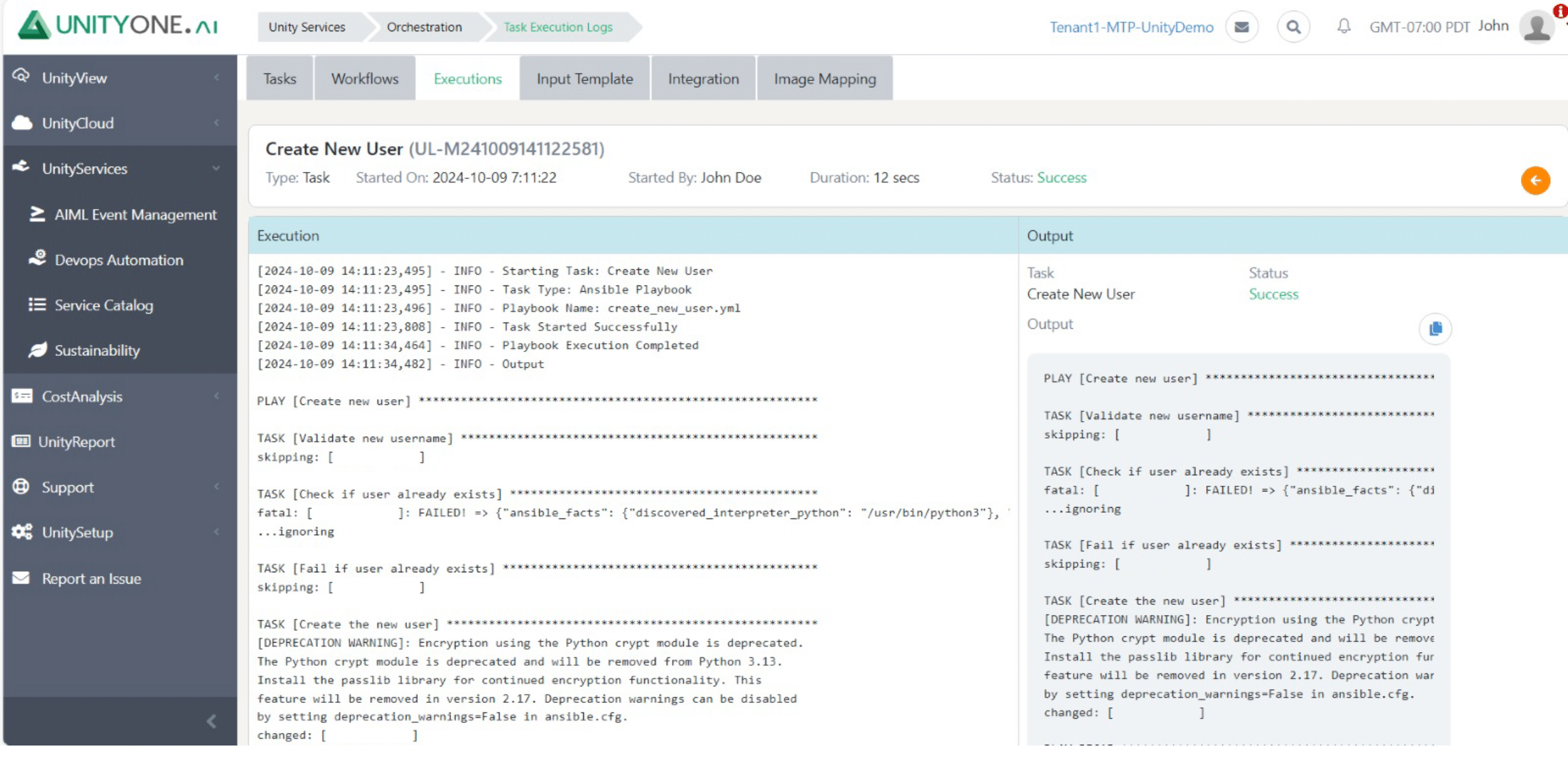
Create New User
Establishing new user accounts ensures that employees have the necessary access to perform their duties while maintaining control over system security.
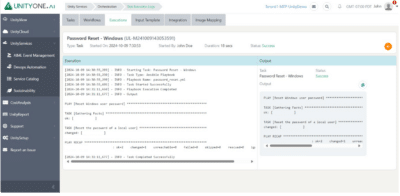
Password Reset
Reporting
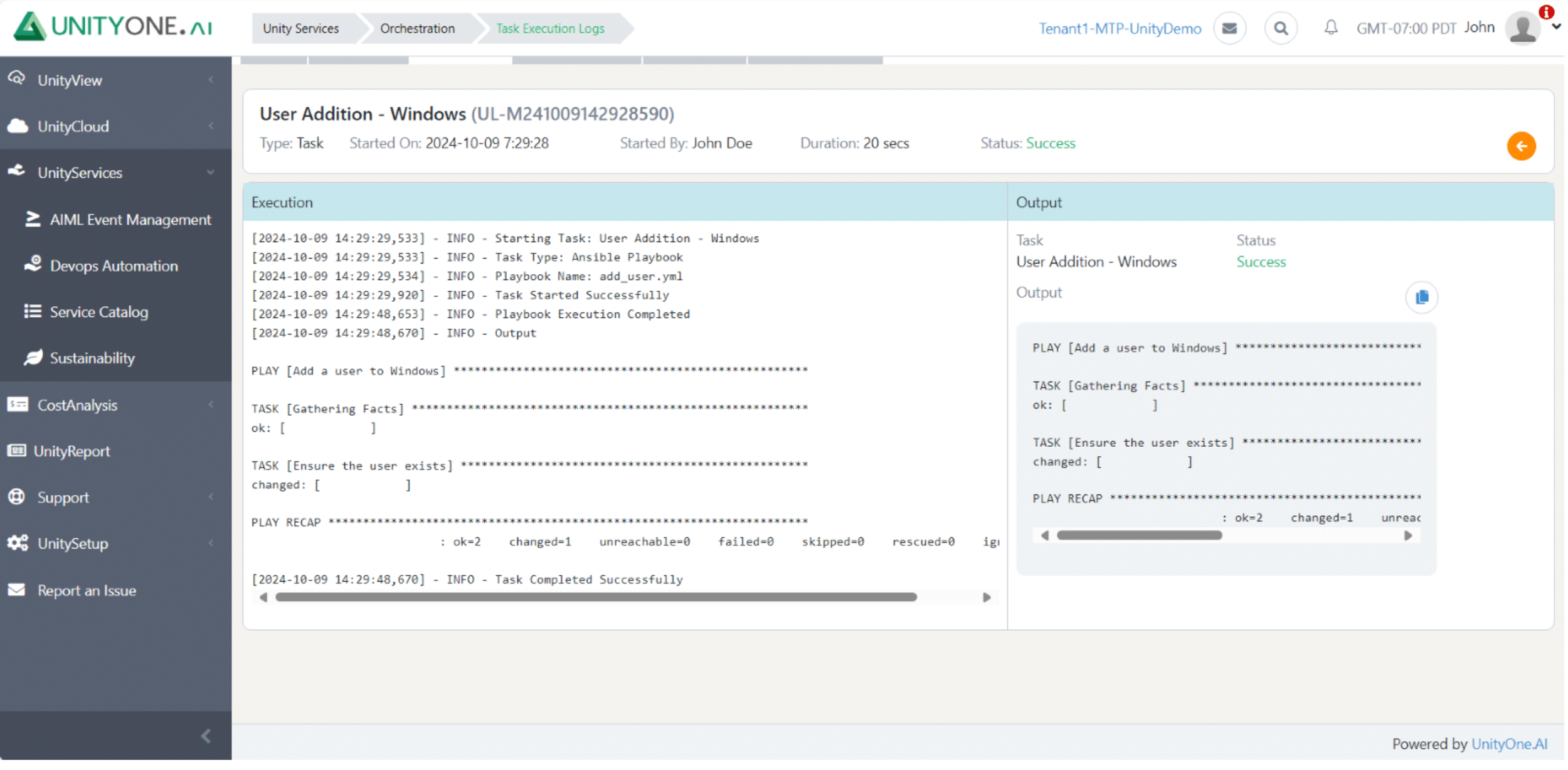
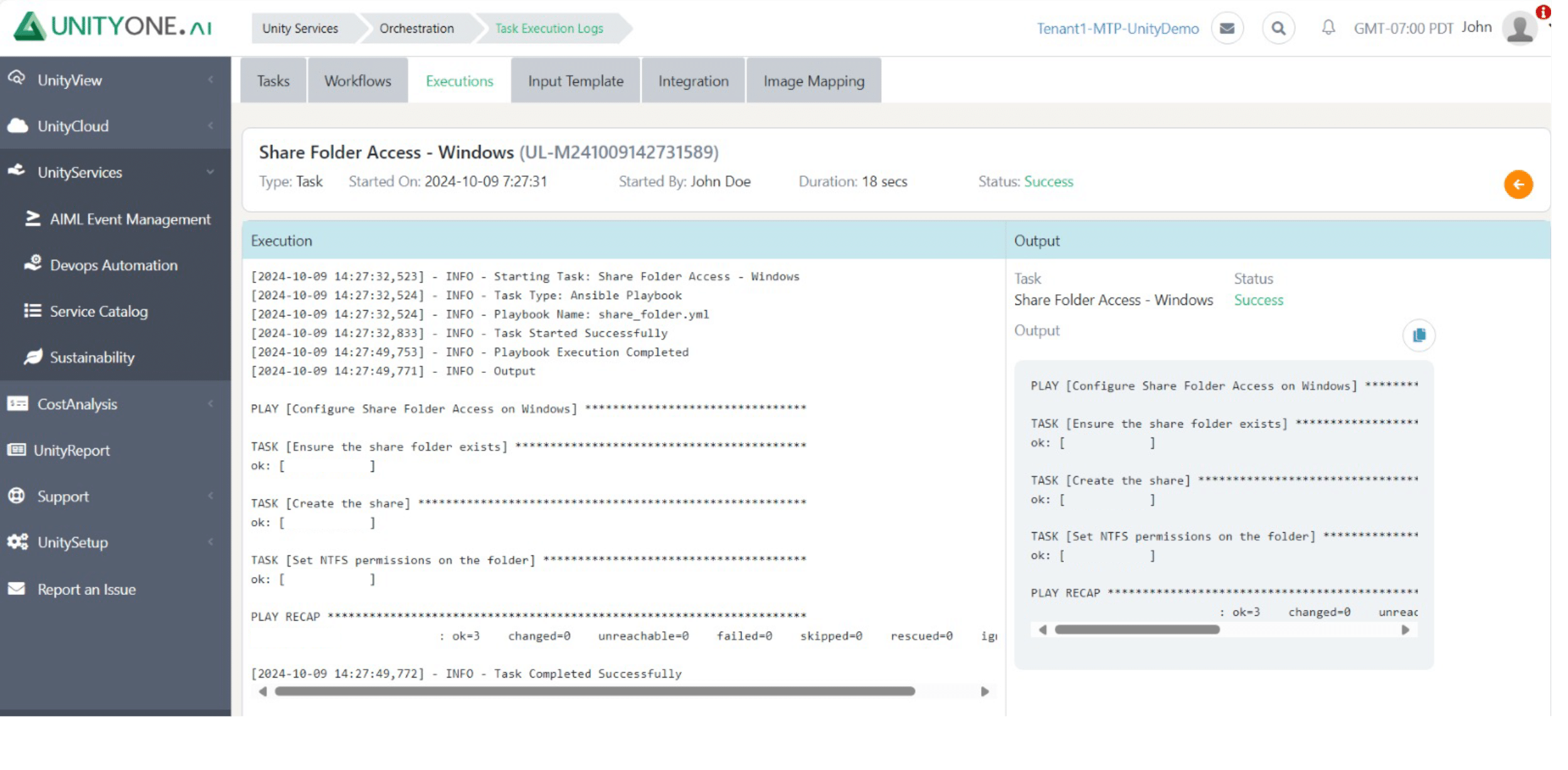
User Addition
User Addition
FAQs
Users can automate tasks in their Hybrid Cloud environment using “DevOps Automation” Module in UnityOne Platform for event-driven automations, Scheduled cron jobs, and infrastructure automation through templates. Additionally, the UnityOne platform allows for scripting and command-line automations as well.
Yes, the user can visualize the complete end to end workflows of the automation tasks and can go deeper dive in each step of workflow to find out any root cause of automation failures.